Why Traditional Security Fails in the Cloud?
For many years, organizations protected their systems using a perimeter-based security model. In simple terms, anyone inside the network was trusted, and anyone outside was not. Firewalls, VPNs, and gateways helped enforce this boundary.
This approach worked when:
- Employees worked on-site using company-managed devices
- Applications and data were stored in private data centers
- Systems rarely changed, and network traffic stayed internal
But today, the environment has changed.
Now:
- Employees access systems from anywhere, often using personal devices
- Data and applications are spread across cloud providers, SaaS platforms, and hybrid environments
- External users such as vendors, partners, and contractors need regular access to internal systems
- Infrastructure is dynamic, with containers, APIs, and cloud resources constantly changing
At the same time, most modern threats don’t attack from the outside. Many breaches now start with:
- Misconfigured cloud storage
- Stolen login credentials or session tokens
- Attackers move quietly within systems once inside
The network perimeter has blurred and, in many cases, no longer exists. Simply trusting internal traffic is no longer enough.
Cloud environments need a new kind of security—one that is flexible, intelligent, and built for constant change.
Why Cloud Environments Need Zero Trust by Design?
Cloud computing has transformed how organizations deploy and scale systems. With its flexibility, scalability, and speed, the cloud empowers innovation, but also introduces new risks.
Contrary to the misconception, the cloud is not naturally unsafe. AWS, Azure, and Google Cloud offer robust native security features. However, the way cloud environments function, distributed, dynamic, and internet-exposed, requires a security model that assumes no implicit trust.
Traditional perimeter-based security cannot keep up with:
- Users and workloads operating outside fixed boundaries
- Constantly changing infrastructure
- Decentralized identity systems and access patterns
This is why modern cloud environments require Zero Trust by design, a model that validates every request, limits exposure, and assumes compromise is always possible.
Zero Trust Model in the Cloud
Zero Trust is not a single tool or solution. It’s a security strategy built on one foundational idea:
Trust no one by default - verify everything.
Instead of relying on fixed perimeters, Zero Trust focuses on three things:
- Who is making the request
- What they’re trying to access
- Under what conditions does the request happen
This approach fits the nature of the cloud, where activity is fast, distributed, and often short-lived. By using real-time context, such as identity, device status, and behavior, Zero Trust helps ensure that every access is appropriate, limited, and secure.
It’s not about blocking access, it’s about making sure the right access is given, at the right time for the right reasons.
Three Core Principles for Zero Trust in Cloud Environments
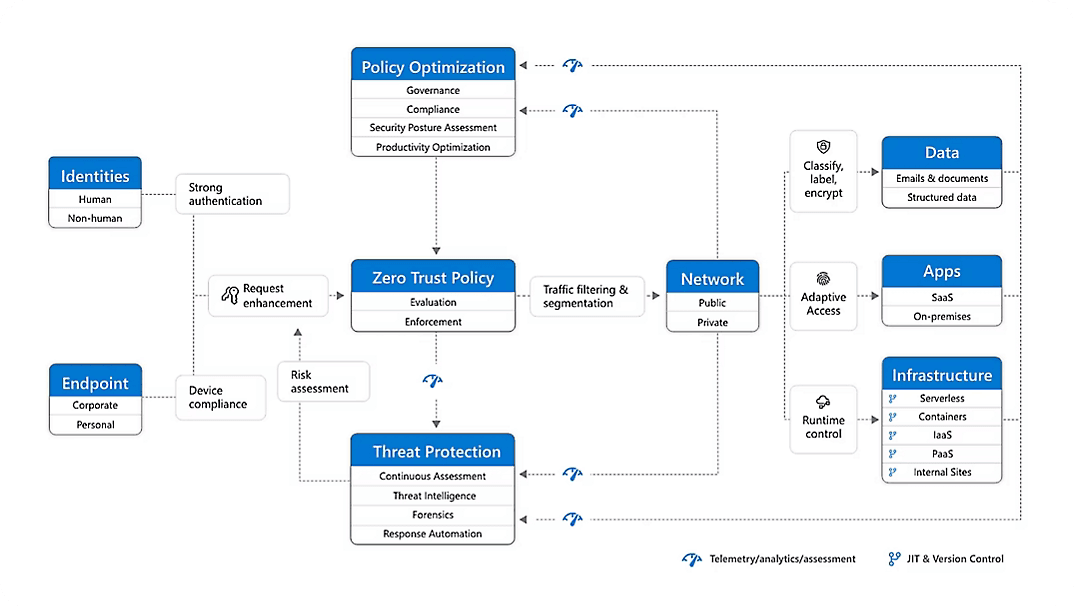
Source - Azure
Zero Trust isn’t about distrust, it’s about removing blind trust from your systems. At its core, it follows three principles. Each one addresses a real security gap in modern cloud environments.
- Always Verify Access
Every request, whether from a user, device, or service, must be verified using real-time data. Instead of relying on a one-time login, Zero Trust checks access continuously based on:
- Identity of the user or workload
- Health and security of the device
- Location and network being used
- Time and method of access
- Sensitivity of the data or system being requested
Cloud platforms provide many of these signals already. Smart use of them enables accurate access decisions without creating friction for users. This approach avoids blind trust and ensures that only authorized requests go through every time.
- Limit Access to Exactly What’s Needed
This is called least-privilege access. It means users and systems only get the exact access they need to do their job, and no more.
In a cloud environment, this could mean:
- A developer has read-only access to production logs, but cannot change live systems
- A finance team member can view billing data, but cannot make changes to the infrastructure
- A third-party vendor can only access one cloud service, during business hours, from a verified device
This reduces the impact of mistakes or attacks. If one account is compromised, the attacker can’t reach everything. Cloud-native tools like IAM policies, role-based access, and temporary permissions make this possible.
- Design for Breach Containment
Zero Trust starts from the assumption that a breach is always possible or may have already happened. This way of thinking is crucial in cloud computing, where systems are connected to the internet.
Rather than focusing only on prevention, this principle adds layers of protection to limit how far an attacker can go:
- Microsegmentation separates systems so attackers can’t move laterally
- Logging and monitoring provide visibility into actions and behavior
- Automated alerts and responses reduce the time it takes to detect and stop a threat
These steps help ensure that even if one part of the cloud is compromised, the rest stays secure.
Clarifying Misconceptions
It’s important to clear up a common misconception:
Zero Trust does not mean locking down systems or making access harder.
When implemented correctly, it allows users to do their work without delay, while ensuring access is always intentional, verified, and limited to what’s necessary.
The result is stronger security that is easy to use, and a better fit for how modern organizations operate in the cloud.
Key Security Challenges in the Cloud
The Shared Responsibility Model
Cloud providers secure the core infrastructure (data centers, hardware, and networking). But everything you build on top of it, your data, applications, identities, and configurations, is your responsibility.
Misunderstanding this division leads to some of the most common and preventable cloud breaches, such as:
- Exposed storage buckets due to misconfigurations
- Overly permissive access controls
- Inadequate monitoring of cloud resources
Without clear ownership and visibility, critical gaps emerge.
Constant Change and Short-Lived Resources
Cloud environments are highly dynamic:
- Resources can be created and removed in seconds
- Workloads are automated and often temporary
- Applications shift across regions or accounts
In such environments, static controls like IP allowlists, manual approvals, or hardcoded credentials fall short. Security must keep up with this pace—automated, real-time, and context-aware.
Multi-Cloud Complexity and Identity Sprawl
Many organizations use more than one cloud platform. Each provider has its own:
- Identity and access management (IAM) framework
- Policy definitions
- Monitoring and logging tools
This leads to:
- Fragmented access controls
- Inconsistent policy enforcement
- Limited visibility across platforms
Attackers exploit these inconsistencies, often entering through the least secure environment.
Why Zero Trust Is the Right Fit?
Zero Trust addresses these challenges head-on. It is built for distributed, fast-moving, and boundaryless systems like the cloud.
It replaces outdated assumptions with real-time, risk-aware decisions based on:
- Who is requesting access
- What device or system is involved
- The sensitivity of the data or workload
- The current context and behavior
Zero Trust allows organizations to:
- Enforce access based on identity and context, rather than physical location or network zones
- Adapt security dynamically, in line with changing workloads and risk signals
- Apply consistent controls across all environments—whether in the cloud, on-premises, or hybrid
By removing blind trust and embedding protection into every layer, Zero Trust makes cloud adoption safer.
Core Components of a Zero Trust Cloud Architecture
To move from theory to real-world protection, organizations need to understand the key components that bring Zero Trust to life in cloud environments.
These building blocks work together to ensure that every access decision is intentional, context-aware, and risk-informed.
Identity and Access Management: The New Perimeter
Zero Trust starts by verifying who is requesting access and whether they should be allowed.
Access isn’t based on location or network anymore, it's based on context and intent. That means even if someone is inside your network or has a login, they shouldn’t be trusted automatically.
To do this effectively:
- Use strong authentication methods, like multi-factor authentication (MFA), to prevent unauthorized access from stolen credentials.
- Centralize identity management across all cloud services using providers like Azure AD, Okta, or Google Identity.
- Apply least-privilege access by assigning roles (RBAC) or setting dynamic conditions (ABAC) to make sure users and workloads only get the permissions they need.
Example: A support engineer can view production logs but cannot modify systems.
Tools: AWS IAM, Azure AD Conditional Access, Google Cloud IAM
Device Trust: Don’t Just Trust the User—Check the Device
Just because a login is valid doesn’t mean the device is safe. If a laptop is outdated, infected, or unmanaged, it could be a security risk — even in the hands of a legitimate user.
Zero Trust includes device checks as part of every access decision. Before granting access:
- Confirm the device is managed by your IT team (via MDM or EDR tools).
- Ensure it's running a secure, up-to-date operating system.
- Check if it has active security tools like antivirus or endpoint detection.
If a device doesn’t meet these standards, its access can be limited or blocked entirely.
Tools: Microsoft Intune, Google Endpoint Management, CrowdStrike Falcon
Data Security: Protect What Matters Most
In Zero Trust, sensitive data is not "safe by default" just because it’s behind a login. Every request to access data is evaluated based on who’s asking, what they’re accessing, and how sensitive that data is.
To protect data in the cloud:
- Classify sensitive data (like customer information, financial records, or source code) so you know what needs the most protection.
- Encrypt data at rest and in transit using strong, cloud-native encryption tools.
- Restrict access based on data sensitivity, not just job title. Even internal employees shouldn’t have access to sensitive data they don’t need.
Tools: AWS Macie, Azure Information Protection, Google Cloud DLP
Network Controls and Microsegmentation: Prevent Lateral Movement
Traditional network security trusts anything inside the perimeter. But in the cloud, where environments are flat and distributed, that model falls apart.
Zero Trust breaks up the network into smaller, isolated zones, so a compromise in one area can’t easily spread to another. This is called microsegmentation.
Alongside segmentation, Zero Trust adds:
- Identity-aware access gateways, which only allow approved users and devices to reach services.
- Conditional access changes access permissions dynamically based on risk factors like device health, user behavior, or location.
Tools: Cloudflare Access, Zscaler Private Access, Google BeyondCorp
Continuous Monitoring and Response: Detect and Contain Threats Early
Zero Trust assumes that breaches will happen. That’s why visibility, detection, and rapid response are essential parts of the model.
In cloud environments, you need centralized monitoring to catch unusual activity across users, workloads, and systems. This means:
- Aggregating logs from all cloud services to a single monitoring platform.
- Using behavior analytics and machine learning to detect patterns like impossible travel, mass downloads, or abnormal usage.
- Automating responses to disable compromised accounts, alert security teams, or isolate infected machines in real time.
Tools: Microsoft Sentinel, AWS GuardDuty, Splunk, Datadog
Each of these components supports the others. Identity, device health, data sensitivity, and user behavior all contribute to smarter, context-driven access decisions. Zero Trust isn’t about complexity — it’s about precision. When implemented thoughtfully, these building blocks give you control without compromise.
Starting Small: A Practical Path to Zero Trust in the Cloud
After understanding the key components of a Zero Trust architecture, the next step is turning those ideas into action. But full adoption doesn’t happen overnight — especially in complex cloud environments. The most effective way to implement Zero Trust is through phased, focused efforts that prioritize high-risk areas, deliver quick security improvements, and avoid disruption.
This section outlines a practical, step-by-step approach to help your team move from strategy to execution
Take Inventory of What You Need to Protect
Before you can control access, you need to know what you're securing. Start by mapping out your core assets:
- Users and their roles
- Business-critical applications and APIs
- Sensitive data (e.g., customer info, financial records)
- Devices connecting to your cloud environment
This visibility helps prioritize where Zero Trust will have the biggest impact.
Apply Least Privilege Access Where It Matters Most
You don’t have to fix every permission on day one. Instead:
- Focus on high-risk areas first: admin accounts, production systems, and sensitive data.
- Review existing access rights and remove anything unnecessary.
- Use roles or attributes to grant the minimum level of access required.
This reduces the damage attackers can do if an account is compromised.
Strengthen Authentication and Add Contextual Checks
Strong access control starts with verifying identity, not just once, but continuously.
- Enforce multi-factor authentication (MFA) across all cloud accounts.
- Add contextual signals to your access decisions: Is the request coming from a managed device? From a risky location? At an unusual time?
- Use conditional access policies that respond to these signals dynamically.
This shifts your security posture from static to adaptive.
Monitor Before You Enforce
Don’t enforce hard rules blindly. First, observe how your systems are being used:
- Enable centralized logging for all cloud accounts and services.
- Use behavior analytics to spot anomalies (e.g., mass downloads, strange logins).
- Identify normal patterns so you can set intelligent, risk-based policies later.
This approach reduces false positives and improves user experience.
Working with a Designated Team or Application
Choose one small, manageable area to test your Zero Trust setup, such as:
- A single internal application
- A remote team with elevated permissions
- Third-party vendors with cloud access
Roll out Zero Trust controls there first. Learn what works, fix what doesn’t, and then scale based on real-world experience.
Real Barriers (and How Smart Teams Handle Them)
Transitioning to Zero Trust can bring up several real-world challenges. Understanding these challenges and knowing how to address them helps you stay on track without getting stuck.
Legacy Infrastructure
Many organizations still rely on older systems that weren’t designed for today’s security needs. These legacy assets often don’t support modern identity verification or network controls, making it tough to apply Zero Trust principles directly.
- Segment legacy systems to isolate them from critical resources.
- Use secure gateways to control access without requiring immediate upgrades.
- Create a phased plan to modernize legacy infrastructure gradually, avoiding disruption.
Organizational Resistance
Security changes can feel disruptive, especially if teams worry that new controls will slow down their work or add complexity.
- Clearly explain why Zero Trust is essential for protecting both data and business operations.
- Emphasize that smart access controls reduce interruptions by preventing breaches.
- Start with pilot projects that show quick wins and build trust within teams.
Tool Fragmentation Across Environments
Using multiple cloud platforms and on-premises systems often results in fragmented identity systems, inconsistent policies, and isolated monitoring.
- Choose tools that work across different clouds and environments to unify security management.
- Centralize logging and use behavior analytics to get a clear picture of access and activity.
- Base policies on real-world usage and risks rather than generic rules to close gaps effectively.
Real-World Impact: What Zero Trust Looks Like in Action
Zero Trust may sound like a high-level strategy, but it's being applied every day by companies facing practical, messy problems — from startups with rapid growth to large institutions juggling complex cloud systems. Here are three examples that show how it works in the real world:
Securing Innovation at a Fintech Startup
This fintech company was scaling fast. With dozens of developers working across cloud environments, they faced a growing risk of credential leakage and untracked access to critical code.
What they did:
- Rolled out MFA and SSO using Okta to secure developer logins
- Limited GitHub access to company-managed devices only
- Applied just-in-time roles in AWS, giving build pipelines access only when needed
Why it matters:
These changes helped them tighten control without slowing down the team. They reduced the chance of an internal breach or misused credentials, critical in a sector where trust and speed go hand-in-hand.
Balancing Openness and Security at a University
Universities need open access for students and to protect sensitive data like grades, payroll, and research. This institution needed to allow remote access without opening the floodgates.
What they did:
- Introduced context-based access policies (e.g., student logins from dorm Wi-Fi vs. unknown foreign IPs)
- Restricting high-risk systems like student records to verified, managed devices
- Used identity-aware proxies to shield backend services from direct access
Why it matters:
They didn’t block access — they shaped it. Students could still use learning platforms freely, while sensitive systems stayed protected. The IT team reduced risk without making the experience painful.
Simplifying Cloud Security for a Global Retailer
This retail giant was juggling multiple clouds: AWS for inventory, Azure for internal apps, and GCP for AI workloads. Security was fragmented and inconsistent.
What they did:
- Adopted Azure AD as a single identity provider across all cloud services
- Created unified access policies that worked across AWS, Azure, and GCP
- Centralized logging and monitoring for better incident detection
Why it matters:
Instead of stitching together different tools on each platform, they unified control at the identity layer. This cut response time to incidents and made compliance audits far simpler.
Choosing Tools That Make Zero Trust Work
Tools help enforce Zero Trust, but their power comes from how well they fit into your overall strategy. Here’s what to focus on:
- Identity Providers: Tools like Okta, Azure AD, and Google Cloud Identity verify who is requesting access. Identity is the foundation for trust.
- Zero Trust Network Access (ZTNA): Services such as Cloudflare Access and Zscaler replace traditional VPNs, giving users secure, limited access to only what they need.
- Monitoring and Detection: Platforms like Microsoft Sentinel and Splunk continuously watch for unusual activity, so threats are caught early.
- Cloud-Native Security: AWS GuardDuty, Azure Defender, and Google Security Command Center offer tailored threat detection within each cloud platform.
Choose tools that work smoothly together and match your cloud environment and security goals, not just the most popular names.
Your Zero Trust Game Plan: A Practical Roadmap
Implementing Zero Trust is a journey, best taken step-by-step. Here’s a phased approach to help you get started and build momentum.
First 30 Days:
- Roll out MFA across your entire organization to secure user access
- Take inventory of users, applications, and cloud assets for full visibility
- Identify and consolidate identity providers to centralize access management
Next 60 Days:
- Apply least-privilege access controls to your most sensitive systems
- Pilot Zero Trust policies with a small team or specific application to learn and adjust
- Enable logging and start monitoring access patterns for anomalies
Next 90 Days:
- Expand Zero Trust policies across all cloud environments
- Introduce device health checks and automated access controls for stronger security
- Train teams and establish repeatable processes for ongoing management and improvement
Roles and Responsibilities for Success
Zero Trust requires collaboration across your organization:
- Security Team: Design and maintain the Zero Trust architecture, set standards
- IT and Engineering: Implement technical controls, keep configurations up-to-date
- Leadership: Promote a cultural shift, allocate resources, and support governance
Final Thoughts
Zero Trust is not about distrusting your users, it’s about recognizing that trust must be earned continuously. In a cloud-first world, where change is constant and boundaries are blurred, Zero Trust offers a strategic, scalable way to protect what matters most.
Start small, think strategically, and move forward with confidence.