Understanding the Cloud Data Lifecycle
Data in the cloud doesn’t just sit in one place. It flows through different stages from being created, stored, shared, processed, and eventually deleted. This journey is called the data lifecycle, and each stage presents its risks. For example:
- When data is being saved to storage, it’s vulnerable to theft if the storage is breached.
- It can be intercepted while being sent over the internet or between cloud services.
- Even archived or backed-up data can be a target if not properly protected.
Understanding this lifecycle helps identify when and where to apply encryption for maximum security. The goal is simple: ensure that data is protected, whether standing still or moving.
The Role of Data Encryption in Cloud Computing
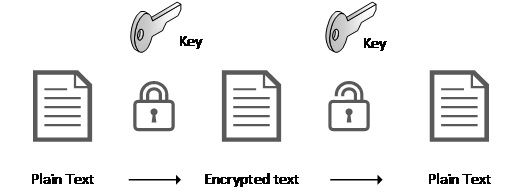
Source - Azure
Encryption is one of the most effective ways to secure data in the cloud. It turns readable data into unreadable text unless you have the right key. This means that even if someone steals the data, they can’t use it.
In a well-rounded cloud security plan, encryption works alongside other safeguards like access control, monitoring, and network security. But what makes encryption stand out is this: it protects data even if all other defenses fail.
Encryption is no longer optional—it’s expected. Whether you’re storing customer records or running a SaaS platform, encryption builds digital trust and meets legal requirements in many industries.
Why Encryption is Essential for Data Protection and Compliance?
Data Privacy, Compliance & Digital Trust
When organizations store personal, financial, or business-critical data in the cloud, they’re expected to keep it safe. Encryption helps ensure that only the right people can access sensitive data.
It’s also a must-have for meeting global privacy laws and standards, such as:
- GDPR (Europe) – Protects the personal data of EU citizens
- HIPAA (U.S.) – Safeguards medical data
- PCI-DSS – Secures credit card and payment data
More than compliance, encryption builds trust with customers. When people know their data is encrypted, they’re more likely to use your app, share personal details, and do business with confidence.
Cloud Security Risks That Make Encryption Necessary
The architecture of cloud computing environments introduces specific security risks that make encryption a critical component of any data protection strategy. Understanding these threats highlights the necessity of encryption in cloud systems.
Common Threats to Data Stored and Transmitted in the Cloud
Cloud-based systems face a variety of potential security threats:
- Data breaches involve unauthorized access to stored information. Cyber attackers often target cloud environments to obtain customer data, financial details, or proprietary business information. Without encryption, any stolen data can be immediately accessed and exploited.
- Man-in-the-middle attacks occur when malicious actors intercept data as it is transmitted between users and cloud servers. If data is not encrypted during transit, intercepted information can be exposed and misused.
- Insider threats stem from individuals who have legitimate access to cloud systems but intentionally or unintentionally misuse that access. This includes employees of cloud providers or account holders whose credentials have been compromised.
- Account hijacking takes place when attackers gain unauthorized control over user accounts, often through stolen login credentials. Once access is obtained, all associated data becomes vulnerable.
The Importance of Protecting Data in Shared Infrastructure Environments
Cloud computing relies on shared infrastructure, meaning multiple customers use the same physical servers and networks. This sharing creates efficiency and cost savings, but it also introduces security concerns.
In a shared environment, your data might sit on the same server as data from other companies. While cloud providers use various techniques to isolate different customers' data, encryption adds an extra layer of protection. Even if someone gains unauthorized access to the physical server, encrypted data remains unreadable without the proper decryption keys.
Encryption ensures that sensitive information remains secure even in multi-tenant environments. It reinforces the overall security posture of cloud systems by mitigating risks associated with shared resources, unauthorized access, and operational vulnerabilities.
What Is Encryption at Rest in the Cloud?
Encryption at rest refers to the protection of data while it is stored on physical media such as disk drives, databases, or other storage systems. In the context of cloud computing, this applies to data that resides in cloud storage and is not actively being transmitted or processed.
Encryption at rest transforms stored data into an unreadable format using mathematical algorithms. The original data gets scrambled using an encryption key, creating what looks like random characters. Only someone with the correct decryption key can convert this scrambled data back into its original, readable form.
The main purpose is to protect stored data from unauthorized access. If someone steals physical storage devices or gains unauthorized access to database files, encrypted data remains useless without the decryption keys.
How Cloud Providers Secure Stored Data?
Leading cloud service providers—including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), offer built-in encryption mechanisms to secure data at rest. Typically, these services automatically encrypt data before writing it to disk and decrypt it when data is accessed, all in a manner that is transparent to the user. This process does not require any manual configuration from customers, and the functionality of applications and services remains unaffected.
Cloud providers generally use robust encryption standards, such as Advanced Encryption Standard with 256-bit keys (AES-256). This widely adopted algorithm is recognized for its high level of security, rendering brute-force attacks impractical with current computational capabilities.
Key Management Options
The management of encryption keys plays a critical role in ensuring the effectiveness of encryption. Cloud providers generally offer two main approaches:
- Provider-managed keys: The cloud provider handles the entire lifecycle of encryption keys, including generation, storage, rotation, and destruction. This approach simplifies key management for customers and is suitable for organizations prioritizing ease of use. However, it also means that the provider retains access to the keys, and by extension, to the encrypted data.
- Customer-managed keys: Customers retain control over their own encryption keys. This may involve generating and storing keys independently or using the provider’s key management services while defining access policies and usage controls. This model enhances data confidentiality, as cloud providers cannot decrypt data without customer authorization. However, it requires a higher level of technical expertise and responsibility from the customer to ensure secure key lifecycle management.
What Is Encryption in Transit in the Cloud?
Encryption in transit protects data as it moves across networks, including transmissions between end-user devices and cloud servers, between different cloud services, and among internal components of distributed cloud applications.
During transmission, data traverses various infrastructure layers such as routers, switches, and communication links. If not encrypted, it is susceptible to interception and unauthorized access by entities monitoring the network. Encryption during transmission ensures that data is securely encrypted before it is sent and only decrypted upon reaching its intended destination.
How is Data Secured While Moving?
Unlike encryption at rest, which occurs once before data is stored, encryption in transit involves continuous encryption and decryption as data flows through networks. This process typically occurs in real time and is designed to be seamless and transparent to end users.
When a user uploads or transmits data to a cloud environment, the originating device encrypts the information. The data is then transmitted over secure channels to the cloud provider, which decrypts it upon receipt for processing or storage. This process protects data from a range of threats, including network eavesdropping, packet sniffing, and man-in-the-middle (MITM) attacks. Even if the data is intercepted during transmission, it remains inaccessible without the appropriate decryption keys.
Common Protocols and Cloud-Specific Implementations
Several established protocols are used to implement encryption in transit:
- Transport Layer Security (TLS): TLS is the predominant protocol for encrypting data transmitted over the Internet. It secures web traffic and communications between applications and cloud services. The presence of "https://" in a URL indicates the use of TLS encryption.
- Virtual Private Networks (VPNs): VPNs create secure, encrypted tunnels for data transmission between on-premises infrastructure and cloud environments. Organizations often use VPNs to maintain secure connectivity between different network locations.
- Cloud-specific protocols: Major cloud providers implement proprietary protocols to enhance security for communication between internal services. For instance, AWS, Azure, and Google Cloud each have platform-specific mechanisms for encrypting traffic between services within their ecosystems.
Cloud-specific protocols are developed by individual cloud providers to optimize security for their platforms. For example, Amazon's AWS uses custom protocols for communication between different AWS services, while Google Cloud has its own encryption methods for internal traffic.
Most modern cloud platforms encrypt data in transit by default. You don't usually need to configure anything special – the encryption happens automatically whenever data moves between systems.
Key Differences Between At Rest and In Transit Encryption
While both types of encryption protect your data, they work in different situations and address different security risks. Understanding these differences helps you make better decisions about cloud security.
| Feature | Encryption at Rest | Encryption in Transit |
| Data State | Stored/static data | Moving/dynamic data |
| When It's Applied | Upon write to disk or persistent storage | During network transmission |
| Common Use Cases | Cloud storage, backups, and database encryption | HTTPS traffic, API calls, VPNs, file transfers |
| Threats Mitigated | Insider threats, physical theft, and data exposure | Network sniffing, MITM attacks, and data tampering |
| Core Technologies | AES-256, HSMs, disk-level encryption | TLS, HTTPS, IPsec, SSL, VPN |
| Performance Impact | Minimal after encryption setup | Low, protocol-dependent |
| Compliance Role | Required by HIPAA, PCI DSS, and GDPR | Also required by HIPAA, PCI DSS, and GDPR |
Lifecycle Behavior and Activation Flow
Encryption methods activate at different stages of the data lifecycle, determining how long data remains protected and under what conditions encryption is maintained. Understanding this behavior helps align security controls with data flow across systems.
Encryption at Rest: Activates During Data Write and Persists Through Storage Lifecycle
This method begins encrypting data when it is stored and keeps it encrypted throughout its time on disk. Whether the data is at rest for seconds or years, protection remains consistent until it is accessed by an authorized process.
How it functions:
- Encrypts data before it is committed to disk, database, or object storage.
- Remains active during backup, replication, and archival.
- Automatically re-engages on data modification or re-storage.
- Decryption is triggered only during read or access operations by authorized entities.
Lifecycle visibility: Ensures that stored data is always protected, even during downtime or system replication.
Encryption in Transit: Activates During Connection Establishment and Terminates Post-Delivery
This method secures data temporarily while it moves across networks or between systems. A new encryption session is established for each transmission event.
How it functions:
- Initiates with session-based protocols (e.g., TLS) before any data leaves the sender.
- Applies encryption on a per-session or per-packet basis.
- Terminates once data reaches its destination and is decrypted by the receiver.
- Re-establishes encryption for each new transmission or session.
Lifecycle visibility: Active only during data movement, offering transient protection between trusted endpoints.
| Aspect | Encryption at Rest | Encryption in Transit |
| Activation Point | When data is written to storage | At the start of each data transmission session |
| Deactivation Point | When data is accessed or read | Upon successful delivery and decryption |
| Duration of Protection | Continuous while data is stored | Temporary, only during transmission |
| Scope of Application | File systems, databases, and object storage | Network connections, APIs, and device communication |
| Reactivation Frequency | Only on data rewrite | Each session, request, or transfer |
Security Breach Impact and Exposure Surface
The type of encryption used, at rest or in transit, directly affects which stages of the data lifecycle remain protected during a security breach. Each method addresses a distinct attack surface and determines how much sensitive information can be exposed if a compromise occurs.
Encryption at Rest: Mitigates Exposure from Compromised Storage Systems
This method protects data residing in persistent storage. Even if attackers gain access to physical disks, database volumes, or cloud storage containers, they cannot read or use the data without decryption keys.
How it prevents or limits data exposure:
- Exfiltrated files or storage snapshots remain unintelligible without the associated decryption keys.
- Cloud platforms apply encryption by default at the infrastructure layer using standards such as AES-256.
- When using customer-managed keys, access control is separated between data and key infrastructure, adding a layer of isolation.
Security benefit: Ensures that unauthorized access to the storage layer does not result in usable data disclosure, provided keys remain secure.
Encryption in Transit: Mitigates Exposure During Network-Based Attacks
This method secures data while it moves between endpoints, such as between users and cloud services or between microservices in a distributed system.
How it prevents or limits data exposure:
- Captured network traffic is encrypted and cannot be decrypted without access to ephemeral session keys.
- Standard protocols like TLS protect against packet sniffing, session hijacking, and man-in-the-middle attacks.
- End-to-end encryption ensures that even intermediaries cannot inspect or modify data during transmission.
Security benefit: Prevents data leakage or tampering during network-based attacks, even in insecure or public communication channels.
| Aspect | Encryption at Rest | Encryption in Transit |
| Primary Protection Objective | Prevents unauthorized access to stored data | Prevents unauthorized access to data during transmission |
| Common Breach Vectors Addressed | Stolen storage devices, misconfigured access, and insider threats | Network interception, session hijacking, and man-in-the-middle attacks |
| Technical Mechanism | Data is encrypted before being written to disk | Data is encrypted before transmission and decrypted upon arrival |
| Typical Enforcement Methods | Platform-level encryption (e.g., AES-256); optional key control | TLS for HTTPS, API calls, inter-service communication |
| Key Exposure Requirement for Attack | Requires access to both storage and decryption keys | Requires interception and successful decryption of TLS-protected traffic |
| Residual Risk Without Encryption | Full data disclosure from compromised storage | Complete visibility of transmitted data and potential session hijacking |
Performance & Overhead
Encryption mechanisms introduce varying degrees of processing overhead depending on when and how encryption is applied. Optimizing performance requires understanding the location, frequency, and intensity of encryption tasks.
Encryption at Rest: Optimized for Persistent Storage Workloads
Encryption at rest is designed for long-term data protection with minimal disruption to active operations. It leverages hardware-accelerated encryption (e.g., AES-NI) at the storage or infrastructure layer, allowing most workloads to operate with negligible impact.
Performance Characteristics:
- Read operations typically experience near-zero latency once data is decrypted into memory.
- Write operations incur marginal overhead due to on-the-fly encryption at the block, file, or application level.
- Asynchronous operations such as scheduled backups, replication, and archival can be encrypted with minimal user-facing performance degradation.
- Hardware acceleration and storage-level integration enable consistent throughput across large-scale datasets.
Encryption in Transit: Real-Time Cryptographic Load During Transmission
Encryption in transit requires continuous, session-based encryption and decryption during data transfer. It introduces real-time performance considerations, particularly in latency-sensitive or high-throughput environments.
Performance Characteristics:
- TLS/SSL handshakes add latency during connection establishment, especially for first-time or frequent short-lived connections.
- Real-time encryption impacts CPU usage during packet processing, especially at high data volumes or concurrency levels.
- Optimizations such as TLS session reuse, connection pooling, and hardware offloading (e.g., TLS accelerators, SmartNICs) mitigate some performance costs.
- Streaming media, APIs, and large file transfers may experience noticeable slowdowns if tuning or load distribution is not properly implemented.
| Aspect | Encryption at Rest | Encryption in Transit |
| Overhead Timing | At time of data write or access | Continuous during each transmission |
| Read Performance Impact | Near-zero after initial decryption | None; data must be decrypted upon receipt |
| Write/Transfer Impact | Minimal, infrastructure-optimized | Higher, affected by handshake latency and stream size |
| Optimization Methods | AES-NI, storage-level integration, asynchronous processing | TLS session reuse, hardware offloading, and connection pooling |
| Use Case Sensitivity | Minimal effect on most workloads | High sensitivity in low-latency or high-throughput systems |
Implementation Architecture
The placement of encryption controls within a system architecture influences scalability, separation of duties, and enforcement complexity. Each method has different deployment and integration considerations.
Encryption at Rest: Implemented at the Storage Layer with Key Isolation Options
At-rest encryption is usually implemented by storage providers or infrastructure layers. It often integrates with cloud-native key management systems and operates without modifying application logic.
Implementation characteristics:
- Enforced at volume, file system, or database layer.
- Can be natively applied by cloud platforms or storage services.
- Supports customer-managed keys via external KMS for added separation of duties.
- Compatible with data versioning, archival, and replication mechanisms.
Deployment flexibility: Requires no modification to client-side logic or APIs.
Encryption in Transit: Enforced at the Communication Layer Between Endpoints
In-transit encryption is enforced between clients, services, or devices. It requires correct configuration across all endpoints and often includes certificate handling and trust management.
Implementation characteristics:
- Relies on TLS/SSL, mTLS, or proprietary secure transport protocols.
- Requires certificate provisioning, renewal, and secure storage.
- Can be enforced through load balancers, service meshes, or API gateways.
- Scales horizontally with distributed services and decentralized endpoints.
Deployment flexibility: Enables granular trust boundaries across microservices, external integrations, or client interfaces.
| Aspect | Encryption at Rest | Encryption in Transit |
| Implementation Layer | Storage systems, file systems, or database engines | Application, network stack, transport protocols |
| Control Integration | Cloud platform encryption or KMS APIs | TLS configuration, certificates, endpoint policies |
| Scalability | Scales with storage tiers and replication policies | Scales with the number of endpoints and session concurrency |
| Application Dependency | Minimal, often transparent to workloads | Requires support for secure protocols and session mgmt. |
| Key Management Responsibility | Centralized (e.g., AWS KMS, GCP CMEK) | Distributed between communicating endpoints |
Why Both Are Required for Complete Data Protection?
Relying on only one form of encryption introduces serious vulnerabilities:
- If only encryption at rest is used, Data is unprotected during transmission. Attackers can intercept sensitive information (e.g., login credentials, session data) while it is in motion.
- If only encryption in transit is used, Data stored on cloud servers, databases, or backup systems can be exposed through unauthorized access or breaches.
Comprehensive data protection requires securing the entire data lifecycle:
- User request: Data is encrypted in transit from the user’s device to the cloud.
- Processing: Encrypted data is accessed from secure, encrypted storage.
- Response: Results are encrypted and transmitted back to the user.
- Logging: Session data is encrypted before being stored in logs or backups.
Failure to implement both encryption types leaves critical gaps exploitable by attackers.
Cloud-Native Encryption Services
Most major cloud platforms offer built-in encryption services that help protect data without needing to build custom solutions from scratch. These tools handle key generation, storage, rotation, and access control, all while integrating with other cloud services.
Here are the leading offerings:
AWS KMS (Key Management Service)
AWS KMS allows you to create and manage cryptographic keys and control their use across AWS services. It supports both customer-managed and AWS-managed keys, and integrates directly with S3, EBS, RDS, Lambda, and more.
Azure Key Vault
Azure Key Vault lets you securely store and manage keys, secrets, and certificates. It offers strong integration with Azure services like Blob Storage, SQL Database, and Azure Kubernetes Service (AKS), supporting automated key rotation and access logging.
Google Cloud KMS
Google Cloud KMS provides centralized key management with support for symmetric and asymmetric encryption. It works with GCP services such as Cloud Storage, BigQuery, and Compute Engine, and offers customer-supplied key support for higher control.
Encryption for Cloud Compliance and Regulations
Encryption plays a critical role in meeting legal and industry compliance requirements. Many regulations don’t just recommend encryption—they mandate it for handling sensitive or personal data.
Here’s how encryption aligns with major frameworks:
| Regulation | Encryption Role |
| GDPR | Requires data protection “by design and by default,” including encryption. |
| HIPAA | Encourages encryption of protected health information (PHI) at rest and in transit. |
| CCPA | Offers liability protection if encrypted personal data is breached. |
| ISO 27001 | Calls for strong encryption policies and documented encryption controls. |
| PCI-DSS | Requires encryption of cardholder data in storage and during transmission. |
Importance of Auditability and Encryption Policy Documentation
Compliance isn’t just about having encryption—it’s about proving you’ve applied it responsibly. That’s where documentation and audit trails come in:
- Maintain clear encryption policies that define which data is encrypted, how keys are managed, and who has access.
- Use automated audit logging to track key usage, decryption requests, and any failed access attempts.
- Keep records of key rotation schedules, configuration changes, and third-party encryption tools in use.
This documentation not only supports audits and regulatory reviews but also improves incident response and internal accountability.
Use Cases in Cloud-Based Systems
Encryption plays a critical role in protecting sensitive workloads across different layers of cloud-native architectures. Below are targeted examples showing how encryption at rest and in transit addresses distinct operational challenges.
Protecting Sensitive Records in Cloud Databases
Encryption at Rest in Practice
Healthcare and financial services use encryption at rest to protect confidential records stored in managed cloud databases. For instance, electronic health records stored in Amazon RDS or Google Cloud SQL are encrypted using AES-256. Even if storage volumes or snapshots are compromised, unauthorized access yields only unreadable ciphertext.
Benefit: Prevents exposure of personal data from compromised storage or database backups.
Securing Internal Traffic in Microservices Architectures
Encryption in Transit in Practice
Microservices deployed on platforms like Kubernetes exchange data continuously. By enforcing mutual TLS (mTLS) between services, platforms such as Istio or Linkerd ensure that sensitive transactions—like authentication tokens or financial data—are encrypted during transmission, even within the internal cluster network.
Benefit: Prevents inspection or tampering of internal traffic by compromised nodes or lateral threats.
End-to-End File Protection in SaaS Applications
Combined Use of Both Encryption Modes
SaaS platforms that support file uploads (e.g., document collaboration tools) apply encryption at multiple stages. Files are encrypted in transit during upload and download using TLS, and encrypted at rest once stored in object storage (e.g., S3 or Azure Blob Storage).
Benefit: Maintains data confidentiality throughout the full file lifecycle—from user to backend and back.
Client-Side Encryption and End-to-End Approaches
Most people are familiar with encryption, which happens when data is stored or transmitted. But there’s another layer of protection that happens even earlier, before data ever reaches the cloud.
In client-side encryption, the data is encrypted directly on the user’s device, and the cloud provider never sees the unencrypted version. This means that even the cloud provider can’t read your data, adding an extra layer of privacy.
End-to-end encryption takes this a step further. It ensures that only the sender and the receiver can read the data, no one else, not even the services transmitting it. Messaging apps like WhatsApp or Signal use this approach.
How Client-Side Encryption Differs from Server-Side Models?
| Type | Where Encryption Happens | Who Holds the Key? |
| Client-Side Encryption | On the user's device | The user or organization |
| Server-Side Encryption | On the cloud provider’s servers | The cloud provider or customer (if BYOK is used) |
With client-side encryption, organizations keep full control. This can improve privacy and help with compliance in industries that require strong data sovereignty.
However, it also means you’re responsible for key management. Lose the key, and you lose the data.
Use Cases: Zero Trust, BYOK, and Privacy-First Models
- Zero Trust Security: This model assumes no one—including internal systems—is trustworthy by default. Client-side or end-to-end encryption fits naturally here, as data is protected at the earliest possible stage.
- BYOK (Bring Your Own Key): Instead of using keys from the cloud provider, you supply your own encryption keys. This gives your organization more control and may help meet strict regulatory needs.
- Privacy-First Services: Apps that promise strong privacy—such as health apps, secure messaging platforms, or encrypted file-sharing services—often rely on client-side or end-to-end encryption to deliver on that promise.
Best Practices for Cloud-Based Encryption
Effective encryption extends beyond enabling a setting. Proper implementation requires strong key management, full-lifecycle coverage, and operational visibility.
Enforce Encryption by Default
Apply encryption consistently across all environments:
- At rest and in transit: Ensure cloud services automatically encrypt data storage and communications. Favor managed services with built-in encryption (e.g., AWS S3 default encryption, GCP’s Transparent Data Encryption).
- Client-side: Where applicable, design apps to encrypt sensitive data before it enters the cloud. This is especially relevant in Zero Trust environments or industries with strict data sovereignty requirements.
- Avoid selective encryption: All data—regardless of perceived sensitivity—should be protected uniformly to reduce attack surface and avoid compliance gaps.
- Integrate early: Bake encryption into application and architecture design from the beginning, not as an afterthought.
Apply Robust Key Management and Rotation Policies
Encryption is only as strong as your control over the keys:
- Use strong standards: AES-256 (symmetric) and RSA-2048 or higher (asymmetric) remain best practice.
- Manage key ownership:
- For server-side encryption, use cloud-native KMS (e.g., AWS KMS, Azure Key Vault, Google Cloud KMS).
- For client-side encryption or BYOK models, ensure your organization securely stores and rotates keys independently.
- Rotate keys regularly: Automate key rotation monthly or quarterly, depending on sensitivity.
- Separate duties: Ensure that individuals or systems managing encryption keys are not the same ones accessing the encrypted data.
Implement Monitoring and Auditing of Encryption Operations
Visibility ensures encryption is working and meets both security and compliance goals:
- Audit logging:
- Record all encryption and decryption operations, along with timestamps, service identities, and user access.
- This includes client-side decryption events when integrated into enterprise platforms.
- Alert on anomalies: Configure alerts for behaviors such as large-volume decryptions, off-hours access, or key misuse.
- Test and validate: Regularly verify that encryption is correctly applied across data types, services, and endpoints — including mobile devices and client software.
- Policy reviews: Audit encryption policies and KMS configurations to ensure compliance with evolving standards (e.g., GDPR, HIPAA).
Moving Forward
Encryption in cloud environments is not just about protecting data — it's about integrating security into every layer of your architecture. By combining strong encryption practices with clear operational controls and continuous monitoring, organizations can reduce risk while maintaining performance, compliance, and user trust.