1. Introduction
1.1 Purpose of the Blog
As cloud adoption accelerates, managing who can access what becomes a critical pillar of any enterprise's security and operational model. Among the many tools and strategies available, Identity and Access Management (IAM), Single Sign-On (SSO), and Federation are often misunderstood or used interchangeably—despite serving distinct purposes. This blog aims to provide a clear, technical comparison of these three identity paradigms, helping architects, security engineers, and platform teams choose the right approach for their cloud strategy.
1.2 Importance of Identity Management in Cloud Strategy
Cloud computing has decentralized infrastructure, but centralized identity is more important than ever. Identity is the new perimeter—controlling user and service access in environments that are inherently dynamic and distributed. Whether you're dealing with a multi-cloud architecture, enabling third-party integrations, or scaling internal access, having the right identity model directly impacts security posture, compliance, and user experience.
A well-chosen identity model not only reduces the risk of breaches but also simplifies governance and improves agility in modern DevOps workflows.
2. Foundations of Identity and Access in the Cloud
2.1 What is Identity in the Cloud Context?
In traditional IT, identity typically referred to on-premises user accounts in Active Directory or similar systems. In the cloud, identity extends beyond human users to include:
- Machines (e.g., VMs, containers)
- Services (e.g., APIs, microservices)
- Applications (e.g., SaaS platforms, internal apps)
These identities must be uniquely identifiable, authenticable, and auditable across multiple environments. Cloud identity also implies distributed trust, often involving external providers or delegated authority.
2.2 Core Concepts: Authentication vs Authorization
Two foundational concepts underpin identity systems:
| Concept | Definition | Example |
| Authentication (AuthN) | The process of verifying who a user or system is. | Logging in using a username and password, or via MFA. |
| Authorization (AuthZ) | The process of verifying what the authenticated entity is allowed to do. | A user can access S3 buckets but cannot delete them. |
It's critical to understand that AuthN must happen before AuthZ, and both require distinct controls. Mistaking one for the other can lead to security holes or overly complex policies.
2.3 Key Stakeholders: Users, Applications, and Services
The identity plane in cloud systems interacts with a variety of stakeholders:
- Users – Human operators, developers, admins, and external partners.
- Applications – Web apps, mobile apps, and third-party SaaS.
- Services – Backend APIs, daemons, and serverless functions that need to authenticate and authorize internally or externally.
Each of these entities needs a distinct identity lifecycle, access policy, and audit trail.
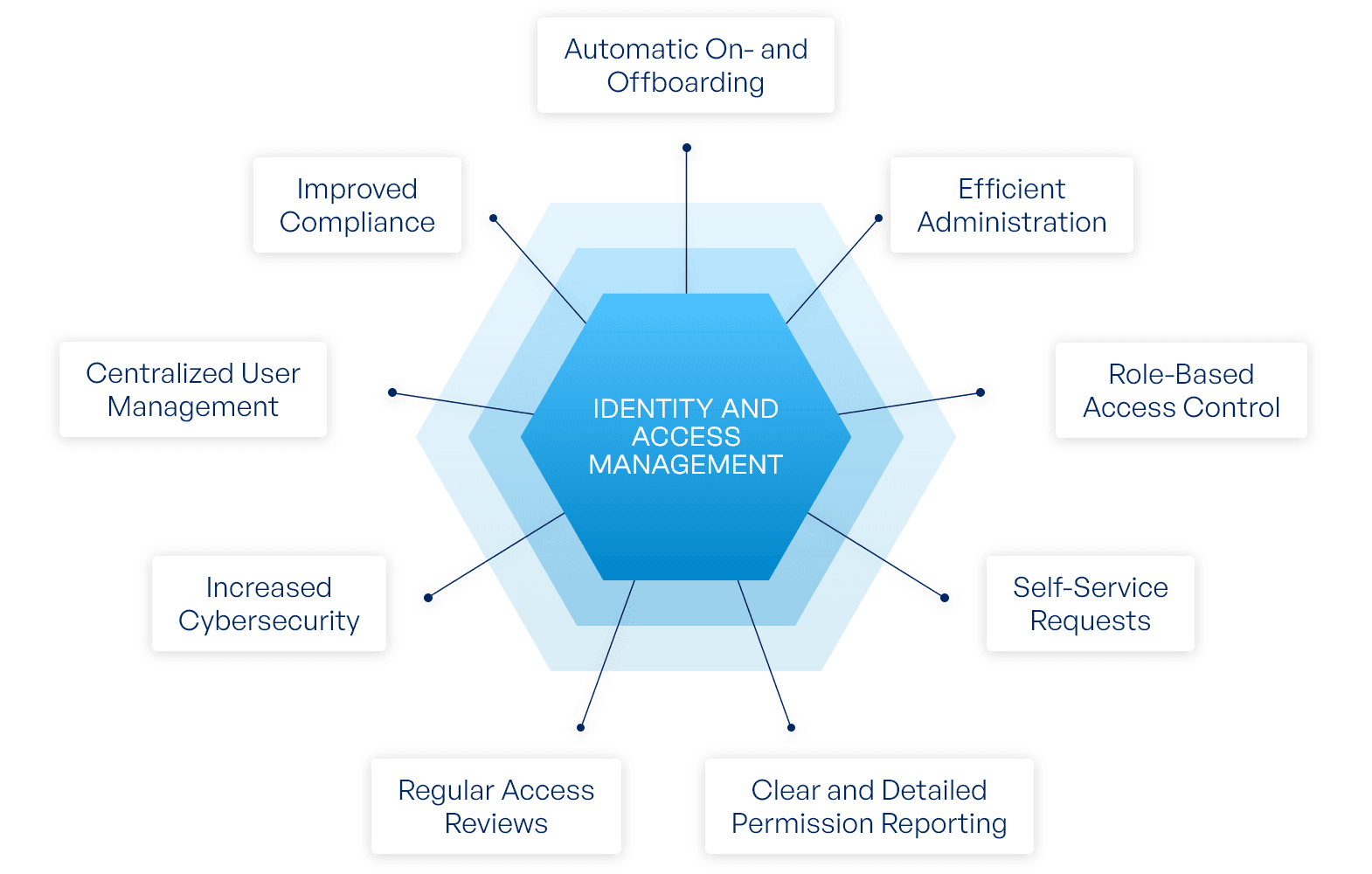
3. What is Identity and Access Management (IAM)?
Source: Tenfold
3.1 Definition and Scope of IAM
Identity and Access Management (IAM) is the discipline of defining and managing the roles, identities, and access rights of users and systems within an environment. In cloud platforms, IAM governs who can take what action on which resource, under what conditions.
IAM is not a login system—it's a policy control layer that sits at the heart of cloud security.
3.2 Core Components of IAM Systems
Most IAM systems, especially in the cloud, consist of these key elements:
- Users and Groups – Represent identities and their associations.
- Roles – Define a set of permissions that can be assumed.
- Policies – JSON-structured documents that declare allowed or denied actions.
- Permissions – Specific operations tied to resources (e.g., s3:ListBucket).
Example IAM Policy (AWS-style):
| json { "Version": "20XX-1X-XX", "Statement": [{ "Effect": "Allow", "Action": ["s3:GetObject"], "Resource": ["arn:aws:s3:::my-bucket/*"] }] } |
3.3 Common IAM Capabilities (RBAC, Policy Management, Auditing)
IAM systems generally offer:
- Role-Based Access Control (RBAC) – Permissions grouped by job functions.
- Policy-Based Access Control (PBAC/ABAC) – Dynamic access based on attributes.
- Audit Logging – Traceable records of identity usage.
- Delegated Access – Granting temporary, scoped permissions to third parties or automated systems.
IAM serves both security and operational scalability, particularly in environments where infrastructure is ephemeral and programmatically managed.
3.4 IAM in Cloud Providers (AWS IAM, Azure AD, GCP IAM)
Each cloud provider offers its own IAM implementation, all sharing similar concepts but differing in syntax and structure.
| Provider | IAM Service | Notable Features |
| AWS | AWS IAM | Fine-grained policy controls, temporary credentials, IAM Roles |
| Azure | Azure AD + RBAC | Hybrid identity integration, conditional access |
| Google Cloud | GCP IAM | Resource-level permissions, IAM Conditions, Workload Identity |
3.5 Strengths and Limitations
Strengths:
- Fine-grained control over resources
- Centralized policy enforcement
- Native integration with cloud services
- Strong audit capabilities
Limitations:
- Not suitable for external identities or cross-org login
- Can become complex at scale without policy hygiene
- Often lacks intuitive user experience for SSO-style login
- Difficult to federate across multiple cloud providers natively
IAM is foundational but not sufficient on its own for multi-cloud, B2B access, or unified login experiences—this is where SSO and Federation come in.
4. What is Single Sign-On (SSO)?
Source: Wallarm
4.1 Definition and Functionality
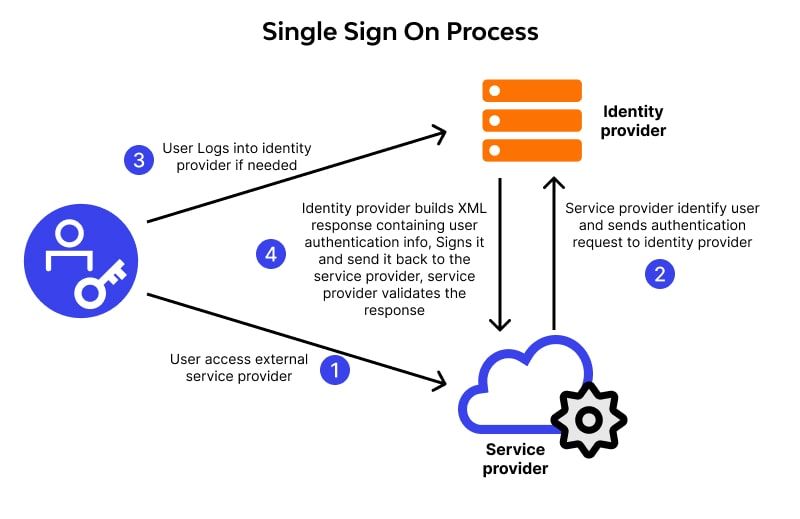
Single Sign-On (SSO) is an authentication method that allows users to log in once and access multiple independent applications or systems without needing to authenticate again for each one. It eliminates the need for users to maintain separate credentials for each service, simplifying access and improving both security and user experience.
SSO relies on a centralized Identity Provider (IdP) to authenticate users and then provides identity assertions to other applications, known as Service Providers (SPs). Once authenticated, the user can navigate across multiple services without re-entering their credentials.
4.2 How SSO Works: Protocols and Flow
SSO implementations use standardized protocols to facilitate trust between IdPs and SPs. The most widely adopted protocols are:
| Protocol | Purpose | Characteristics |
| SAML 2.0 | Web-based enterprise SSO | XML-based; mature and widely adopted in corporate environments |
| OpenID Connect (OIDC) | Web and mobile applications | JSON-based; built on top of OAuth 2.0; modern and flexible |
| OAuth 2.0 | Authorization | Delegates access using tokens; not designed for authentication but often paired with OIDC |
Example: OpenID Connect (OIDC) Flow
- User attempts to access an application (SP).
- The application redirects the user to an Identity Provider (IdP).
- The user authenticates with the IdP.
- The IdP issues an ID token and redirects the user back to the application.
- The application verifies the token and establishes the session.
This flow enables secure, token-based access without requiring the user to log in to each service individually.
4.3 Benefits and Use Cases of SSO
Benefits:
- Improved User Experience: Reduces password fatigue by minimizing login prompts.
- Stronger Security: Fewer credentials mean a smaller attack surface and better enforcement of policies like MFA.
- Simplified Identity Management: Centralized authentication makes provisioning and deprovisioning faster and more reliable.
- Compliance Support: Centralized logs and consistent session behavior aid in audit and compliance efforts.
Common Use Cases:
- Internal enterprise applications (e.g., HR, finance, intranet portals)
- SaaS integration (e.g., Salesforce, Slack, GitHub)
- Workforce access management for hybrid or remote teams
4.4 Limitations and Security Considerations
Despite its advantages, SSO also introduces some architectural and security trade-offs:
- Single Point of Failure: If the IdP is compromised or unavailable, access to all dependent systems is affected.
- Session Hijacking Risks: Improper token handling can lead to replay or impersonation attacks.
- Access Creep: Without careful role and access management, users may accumulate more privileges than necessary.
- Complexity of Integration: Legacy systems may not support modern SSO protocols, requiring workarounds.
Mitigating these risks requires implementing controls such as short token lifetimes, strong session management, and mandatory MFA.
4.5 SSO in Practice
Examples:
- Google Workspace: Supports SAML-based SSO to external applications, allowing users to authenticate once with their Google account.
- Okta: Offers cloud-based SSO across thousands of SaaS and on-premises applications, with support for OIDC and SAML.
- Azure Active Directory: Provides SSO capabilities integrated with Microsoft 365, Azure services, and third-party apps.
- Auth0: Developer-focused platform supporting OIDC and social logins, often used in customer-facing applications.
These platforms offer extensive SDKs, connectors, and management tools to streamline SSO adoption.
5. What is Federation?
Source: Springer
5.1 Definition and Key Concepts
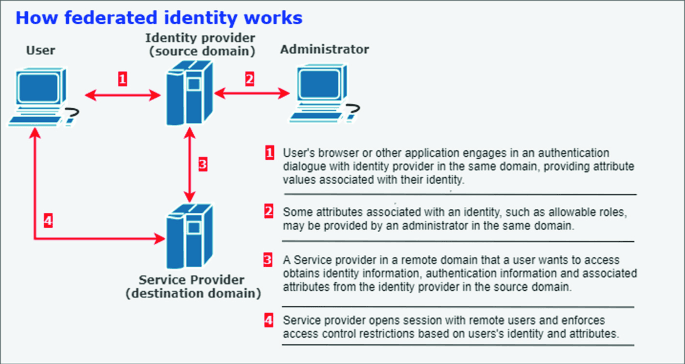
Federation is a mechanism that enables authentication across different identity domains. It establishes trust between independent organizations or identity systems, allowing a user to authenticate with one organization and access resources in another without creating a new account.
In a federated identity model:
- Identity Providers (IdPs) authenticate users in their home domain.
- Service Providers (SPs) or Relying Parties (RPs) accept authentication assertions from trusted IdPs.
This model allows organizations to retain control over their identity management while enabling secure inter-domain access.
5.2 Federation vs SSO: What’s the Difference?
Though SSO and Federation both simplify access, they serve different purposes:
| Aspect | SSO | Federation |
| Scope | Within one organization | Across multiple organizations or identity systems |
| Authentication | Centralized via single IdP | Delegated to external IdPs via trust relationships |
| Identity Ownership | Single domain | Distributed across trusted domains |
| Example | Access multiple internal systems with one login | Login to a partner’s portal using your company credentials |
SSO can exist within a federated system, but federation explicitly enables cross-boundary identity exchange.
5.3 How Federation Works
A federation is established through:
- Trust Relationship: Configured using metadata, digital certificates, and agreed protocols.
- Identity Assertion: The IdP issues a signed token asserting the identity of the user.
- Relying Party Validation: The SP verifies the token and grants access.
This requires synchronized clocks, secure certificate handling, and well-defined attribute mappings between the domains.
5.4 Protocols Enabling Federation
- SAML 2.0: Common in enterprise-to-enterprise scenarios; supports signed identity assertions.
- OpenID Connect (OIDC): Used in cloud-native and modern B2B environments; lightweight and API-friendly.
- WS-Federation: Microsoft’s legacy protocol for federated identity, still in use in older ecosystems.
5.5 Federation Use Cases
- Business-to-Business (B2B): Vendors or contractors accessing enterprise systems using their own corporate credentials.
- Higher Education: Universities allowing students to access consortium services using their institutional login.
- Multi-National Organizations: Subsidiaries and partners using different identity systems federated into a parent organization.
5.6 Benefits and Trade-Offs
Benefits:
- Reduced Identity Duplication: Users retain their existing credentials.
- Autonomy: Each organization controls its own users and policies.
- Scalable for External Access: Ideal for B2B, consortiums, and multi-tenant SaaS applications.
Trade-Offs:
- Implementation Complexity: Requires coordination between IdPs and SPs.
- Trust Management: Certificates, token lifetimes, and metadata must be carefully managed.
- Limited Visibility: The relying party may have limited insight into user behavior or group memberships.
6. Comparative Analysis: IAM vs SSO vs Federation
6.1 Scope and Functionality Comparison
| Feature | IAM | SSO | Federation |
| Access Control | Yes | No | No |
| Authentication | Yes | Yes | Yes |
| Cross-Domain Support | No | Limited | Yes |
| Identity Governance | Strong | Moderate | Weak (delegated) |
| Best Use Case | Resource-level access control | Internal application access | Partner and third-party access |
6.2 Control Boundaries and Trust Models
- IAM: Operates within the cloud provider boundary, with centralized control over access to resources.
- SSO: Operates within the enterprise boundary; establishes implicit trust among internal applications.
- Federation: Operates across organizational boundaries; trust is explicitly configured through cryptographic and policy agreements.
6.3 Security and Compliance Perspectives
Each model presents different challenges:
- IAM offers fine-grained access control, which is critical for audit and compliance.
- SSO improves credential hygiene, reducing the chance of compromised credentials.
- Federation introduces external trust relationships, which require rigorous vetting and monitoring.
6.4 Scalability and Integration Complexity
| Factor | IAM | SSO | Federation |
| Setup Complexity | Moderate | Low to Moderate | High |
| Scalability (users) | High | High | High |
| Scalability (domains) | Low | Low | High |
| Management Overhead | Medium | Low | High |
Federation is the most complex but also the most extensible across organizations.
7. Choosing the Right Approach for Your Cloud Strategy
7.1 Key Decision Factors
When selecting between IAM, SSO, and Federation, consider the following:
- Organization Size: Larger enterprises often require all three working together.
- Multi-Cloud Usage: IAM strategies vary by provider; SSO and Federation provide consistency across platforms.
- External Access Needs: Federation is necessary for B2B, customer portals, and multi-tenant SaaS platforms.
- Security Posture: MFA, token lifecycle, and centralized audit trails are essential regardless of model.
7.2 Common Deployment Patterns and Architectures
- Startup or Small Teams: May rely solely on cloud IAM with minimal configuration.
- Growing Organizations: Implement SSO to reduce friction and increase user security.
- Enterprises: Deploy federated identity to integrate partner ecosystems and manage external collaboration.
- Hybrid Approaches: Combine IAM for internal policies, SSO for UX, and Federation for B2B.
7.3 Real-World Scenarios and Which Solution Fits Best
Scenario | Best Fit |
| Developer access to cloud resources | IAM |
| Employee access to multiple internal tools | SSO |
| Vendor access to enterprise portal | Federation |
| M&A with disparate identity systems | Federation |
| Cloud-native CI/CD pipelines | IAM |
7.4 Combining IAM, SSO, and Federation: Best Practices
Most mature organizations use a hybrid model:
- IAM governs internal cloud resource access.
- SSO offers seamless user experience across internal applications.
- Federation enables secure collaboration with external entities.
Best Practices:
- Enforce MFA across all authentication points.
- Implement just-in-time provisioning in federated setups.
- Regularly audit roles, permissions, and trust relationships.
- Use centralized logging for incident response and compliance.
8. Security Implications and Risk Management
Identity isn't just a tool for access—it's a foundational control surface in cloud security. As organizations shift more workloads to the cloud, the identity layer becomes a prime target for attackers. Each identity approach—IAM, SSO, and Federation—brings different security considerations and risk vectors.
8.1 Threats and Attack Vectors per Approach
The attack surface varies depending on how identity is implemented.
| Identity Model | Primary Risks |
| IAM | Misconfigured policies, privilege escalation, over-permissioned roles, static credentials |
| SSO | IdP compromise, token theft or misuse, weak session control |
| Federation | Trust mismanagement, outdated metadata, vulnerabilities in external IdPs |
For example, with IAM, assigning overly broad permissions or failing to rotate access keys can allow attackers to escalate privileges and access sensitive cloud services. Misuse of IAM roles in automated pipelines is a frequent source of accidental exposure.
SSO consolidates authentication, but also centralizes risk. A breach at the identity provider could compromise all connected apps. Attackers often target tokens—especially if session expiration and revocation policies are lax.
In Federated environments, trust relationships are critical. If one organization improperly secures its identity infrastructure, it can inadvertently expose its partners. Federation demands robust validation of identity assertions, proper configuration of SAML/OIDC flows, and active monitoring of partner metadata.
8.2 Best Practices for Secure Identity Management
Regardless of the model, securing identity systems requires consistency, visibility, and control:
- Enforce Multi-Factor Authentication (MFA): Especially for privileged users and external access points.
- Apply the Principle of Least Privilege: Ensure users and services have only the permissions they require.
- Conduct Regular Access Reviews: Periodically verify access rights, particularly for long-tenured accounts or service roles.
- Rotate Secrets and Tokens: Set automated rotation intervals and expiration for credentials.
- Monitor for Anomalies: Integrate identity logs with SIEMs to detect unusual login patterns or escalations.
Additionally, enable session management policies—including idle timeouts and forced re-authentication—for high-risk applications.
8.3 Compliance and Regulatory Requirements
Identity systems play a crucial role in meeting industry and regional compliance requirements:
- GDPR: Requires data minimization, strong access controls, and breach notification procedures. Identity platforms must ensure secure user authentication and traceable access.
- HIPAA: Mandates audit trails and role-based access to protect health information. Identity enforcement should tightly control access to ePHI.
- PCI-DSS: Requires multifactor authentication, session timeouts, and immediate revocation of access when roles change.
- SOC 2 and ISO 27001: Expect clear, documented identity governance processes and access control audits.
Meeting these standards is not simply a checkbox exercise—it also demonstrates operational maturity and builds customer trust.
8.4 Identity Governance Considerations
Identity governance extends beyond access—it answers the “who, what, and why” behind each permission. It’s critical to ensure that access is always appropriate, revocable, and justifiable.
A strong governance program includes:
- Role lifecycle management: Roles should evolve with business needs, and be removed when obsolete.
- Automated provisioning and deprovisioning: Leverage HR systems or authoritative sources to manage identities automatically.
- Attestation workflows: Require managers or data owners to periodically review access rights.
- Segregation of Duties (SoD): Prevent conflicts of interest (e.g., a user who can both request and approve access).
When governance is embedded into identity workflows, it reduces the risk of privilege creep, insider threats, and audit gaps.
9. Implementation Considerations
Selecting and deploying an identity solution involves more than comparing features. Success depends on how well the system integrates into your current architecture, scales with your needs, and aligns with operational realities.
9.1 Integration with Existing Systems
Most organizations deal with heterogeneous environments—legacy applications, cloud-native services, and on-prem directories. Seamless identity integration requires:
- Protocol Support: Many legacy systems only support LDAP or custom SSO mechanisms. Modern systems lean on SAML, OAuth2, or OIDC.
- Directory Synchronization: Syncing users from on-prem Active Directory to cloud-based IdPs like Azure AD is often necessary.
- Custom Connectors: For bespoke or industry-specific tools, a custom identity bridge may be needed to enforce unified access.
Pre-deployment testing is critical. Mismatched attribute mappings or token configurations can silently fail, leading to access disruptions or authentication bypasses.
9.2 Tools, Providers, and Platforms
Choosing the right identity provider depends on your technical environment and identity use cases:
| Provider | Strengths |
| Okta | Broad SSO ecosystem, easy to configure, strong MFA |
| Auth0 | Developer-friendly APIs, customizable authentication flows |
| Azure AD | Seamless Microsoft 365 integration, hybrid identity support |
| Ping Identity | Strong in federation, supports complex enterprise use cases |
| AWS/GCP IAM | Native cloud resource management, essential for DevOps and automation |
Many organizations opt for a multi-layered approach—using cloud-native IAM for infrastructure and a dedicated IdP for user access and federation.
9.3 Performance, Latency, and Availability
Since identity systems sit on the access path to every resource, any latency or downtime can cause widespread disruption. Consider the following:
- Redundancy and Failover: Ensure the IdP can operate across regions or availability zones.
- Token Lifespan Configuration: Balance security (short-lived tokens) with usability (session continuity).
- Edge Optimization: For globally distributed teams, edge-accelerated IdPs or localized validation endpoints reduce login lag.
SSO and Federation systems should be treated as critical infrastructure with SLAs, uptime monitoring, and disaster recovery plans.
9.4 Cost and Licensing Factors
Identity costs are often underestimated. Commercial solutions are typically priced per user or per monthly active user (MAU), but costs also arise from:
- Connector licenses: Integrating legacy apps may incur separate fees.
- Advanced features: Governance, reporting, and adaptive access control are often gated behind premium tiers.
- Support and training: Ongoing operational costs increase with complexity.
While cloud-native IAM may appear cost-effective, combining it with SSO and Federation usually requires a dedicated identity budget line.
10. Conclusion
10.1 Recap of Key Differences and Use Cases
Understanding where each identity approach excels is key to making an informed decision:
- IAM is foundational for infrastructure-level access in cloud platforms. It's essential for service-to-service communication, automation, and internal control.
- SSO reduces user friction by centralizing authentication, ideal for employees accessing multiple apps.
- Federation extends identity trust beyond organizational boundaries—critical for B2B partnerships and multi-tenant SaaS scenarios.
Each model solves a distinct challenge, and none are mutually exclusive.
10.2 Strategic Recommendations
An effective cloud identity strategy typically combines these components. Organizations should:
- Start with IAM to enforce fine-grained permissions at the cloud resource level.
- Integrate SSO as soon as users need access to multiple systems or SaaS tools.
- Introduce Federation when collaborating with partners, vendors, or subsidiaries under separate identity systems.
Complement this with a strong governance layer and continuous monitoring to ensure that access remains appropriate, auditable, and secure.