1. Introduction
1.1 Understanding CI/CD Concepts and Benefits
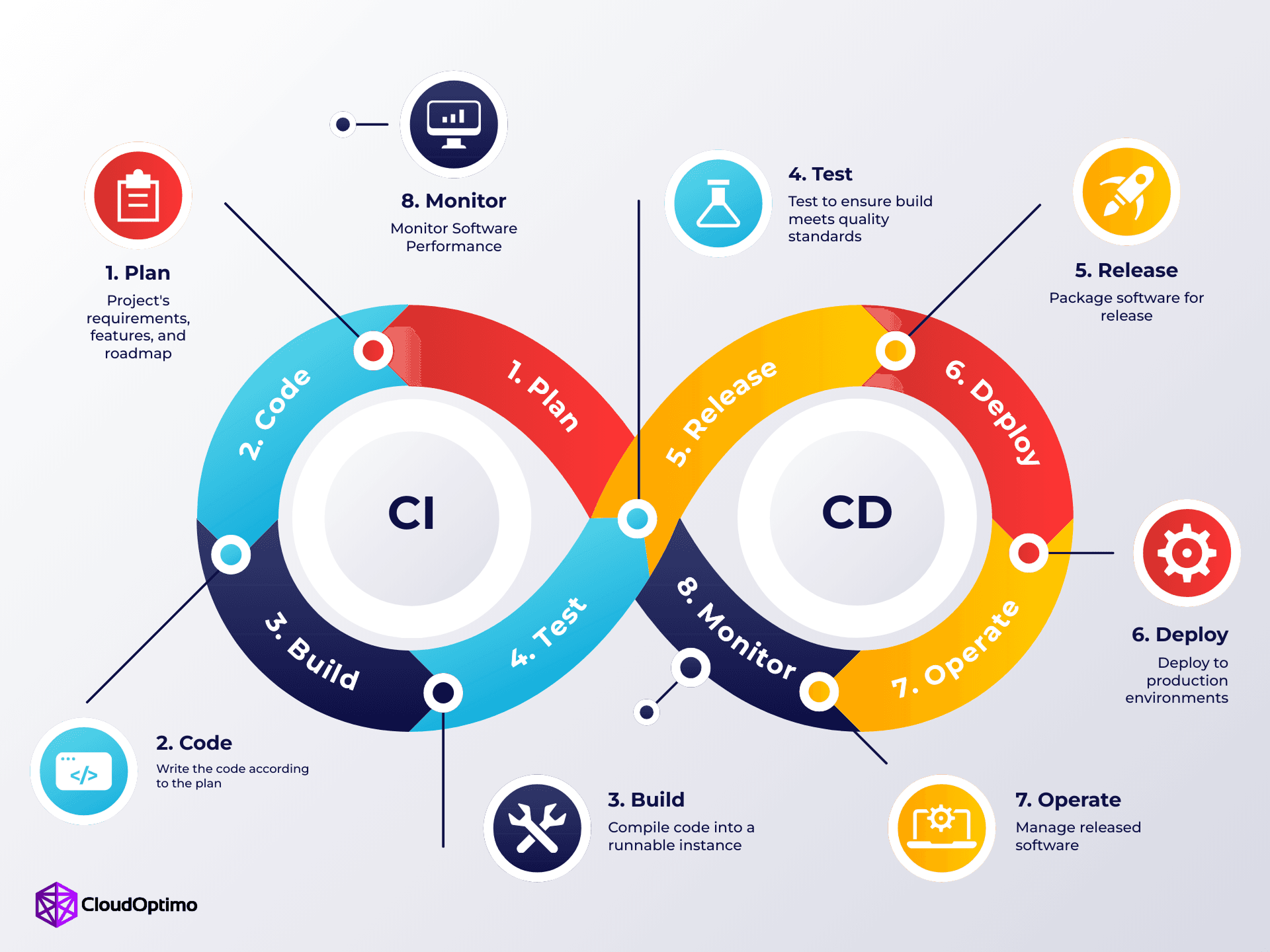
Continuous Integration and Continuous Delivery/Deployment (CI/CD) has become essential in modern software development. CI/CD automates the software delivery process, enabling teams to deliver changes frequently and reliably.
Continuous Integration (CI) involves automatically integrating code changes from multiple contributors into a shared repository. Each integration is verified through automated builds and tests to catch problems early. CI helps developers identify bugs quickly, reduce manual effort, maintain code quality, and work in parallel.
Continuous Delivery/Deployment (CD) extends CI by automating the delivery of applications to selected environments. While continuous delivery ensures code can be reliably released at any time (with manual approval for production), continuous deployment automatically deploys every change that passes tests directly to production without human intervention.
Key benefits of CI/CD include:
- Faster time to market
- Improved developer productivity
- Higher software quality
- Reduced deployment risk
- Better process visibility
- Enhanced team collaboration
1.2 Why Compare GitHub Actions and AWS CodePipeline
Selecting the right CI/CD tool is a strategic decision with long-term implications. GitHub Actions and AWS CodePipeline represent two different approaches:
- GitHub Actions integrates deeply with the GitHub ecosystem, offering a streamlined developer experience.
- AWS CodePipeline is part of AWS's cloud platform, providing robust integration with AWS services.
Understanding their differences is crucial for several reasons:
- Technical fit: Each platform has distinct strengths and limitations that may align better with specific project requirements.
- Operational costs: The pricing models differ significantly, affecting total cost of ownership.
- Team expertise: Your team's familiarity with GitHub or AWS ecosystems can influence implementation success.
- Future flexibility: The choice may impact your ability to adapt to changing requirements.
- Organizational alignment: Alignment with broader technology decisions may influence CI/CD tooling choices.
2. Platform Overview
2.1 GitHub Actions: Core Concepts and Architecture

Source: DevOps.dev
GitHub Actions is a CI/CD platform that automates build, test, and deployment pipelines directly within GitHub repositories. Its core components include:
- Workflows: YAML files in the .github/workflows directory that define automated processes
- Events: Triggers that initiate workflows (push, pull request, scheduled events, etc.)
- Jobs: Sets of steps that execute on the same runner
- Steps: Individual tasks within a job that run commands or actions
- Actions: Reusable units of code for common tasks
- Runners: Servers that execute workflows (GitHub-hosted or self-hosted)
GitHub Actions follows a workflow-based architecture where each workflow operates independently. When an event occurs, the workflow scheduler allocates runners to execute jobs in parallel by default, with steps running sequentially within each job.
| yaml name: Basic CI on: [push, pull_request] jobs: test: runs-on: ubuntu-latest steps: - uses: actions/checkout@v3 - uses: actions/setup-node@v3 - run: npm ci - run: npm test |
2.2 AWS CodePipeline: Core Concepts and Architecture

AWS CodePipeline is a fully managed continuous delivery service that automates release pipelines. Its core components include:
- Pipeline: The end-to-end process for software changes
- Stages: Logical divisions in a pipeline (source, build, test, deploy)
- Actions: Tasks performed within a stage
- Transitions: Connections between stages
- Artifacts: Files produced by and passed between actions
- Artifact Store: S3 bucket storing pipeline artifacts
CodePipeline follows a linear, stage-based architecture where each stage must complete before the next begins. When changes are detected in the source, CodePipeline initiates execution and progresses linearly through stages, with optional approval actions between stages.
| yaml # Simplified AWS CloudFormation example MyPipeline: Type: AWS::CodePipeline::Pipeline Properties: Stages: - Name: Source Actions: - Name: Source # Source configuration - Name: Build Actions: - Name: BuildAction # Build configuration - Name: Deploy Actions: - Name: DeployAction # Deploy configuration |
2.3 Key Differentiators at a Glance
| Aspect | GitHub Actions | AWS CodePipeline |
| Primary Ecosystem | GitHub repositories | AWS cloud services |
| Execution Model | Distributed parallel jobs | Linear sequential stages |
| Configuration | YAML files in repository | AWS Console, CLI, or IaC tools |
| Event Triggers | Rich GitHub event system (40+ types) | Limited source triggers |
| Storage | Ephemeral with artifacts | S3-based artifact store |
| Authentication | GitHub Secrets and OIDC | AWS IAM roles |
| Cost Structure | Minutes-based with free tier | Pay-per-pipeline-execution |
| Self-hosting | Self-hosted runners available | AWS-managed infrastructure |
3. Technical Comparison
3.1 Configuration and Syntax
GitHub Actions and AWS CodePipeline differ significantly in how they handle configuration, with each aligning with the overall structure and purpose of their respective platforms.
- GitHub Actions:
- Configuration is stored in YAML files under .github/workflows/ in the repository.
- Version-controlled alongside your application code, meaning changes go through the same review process as code updates.
- Uses a declarative syntax, incorporating expressions like ${{ expression }} to define jobs, steps, and triggers.
- AWS CodePipeline:
- Configuration is defined separately from the application code, typically through the AWS Console, CLI, or Infrastructure as Code (IaC) tools like CloudFormation.
- Follows the AWS resource model, where pipelines, actions, and stages are treated as AWS resources.
- Can be configured either programmatically or visually via the AWS Console’s graphical interface.
Key Differences:
| Aspect | GitHub Actions | AWS CodePipeline |
| Configuration Location | Stored with application code | Separate from application code |
| Configuration Format | YAML files | AWS resource definitions |
| Syntax Type | Declarative with expressions | AWS resource model, parameter-based |
3.2 Integration with Source Code Management
- GitHub Actions:
- Provides native integration with GitHub repositories, making it easy to trigger workflows directly based on GitHub events.
- Supports 40+ event types (push, pull request, issue comment, etc.), which provide rich context and flexibility in triggering workflows.
- Simple integration with GitHub repositories through actions/checkout, and allows for advanced filtering on branches and paths.
- AWS CodePipeline:
- Requires explicit configuration to connect with various source repositories, including AWS CodeCommit, GitHub, Bitbucket, and Amazon S3.
- Typically, it supports commit-based or manual triggers, with fewer event-driven options compared to GitHub Actions.
- The connection to source repositories needs to be managed separately as resources within AWS.
Key Differences:
| Aspect | GitHub Actions | AWS CodePipeline |
| Repository Integration | Native GitHub integration | Multiple source provider support |
| Trigger Events | 40+ GitHub event types | Primarily commit-based/manual |
| Branch/Path Filtering | Advanced filtering | Basic filtering options |
3.3 Pipeline Structure and Components
- GitHub Actions:
- Uses a job-based structure, where each job can run in parallel or depend on other jobs.
- Each job runs on a specified runner, allowing flexibility in environment setup (e.g., Ubuntu, Windows, macOS).
- Supports complex workflows with conditional execution and matrix builds, enabling parallel testing across different configurations.
- AWS CodePipeline:
- Follows a sequential stage-based model, where stages execute one after another, with each stage completing before the next begins.
- Actions within stages can run in parallel, but the overall pipeline follows a linear progression, and artifacts pass from one stage to the next.
- The pipeline structure is simpler but often better suited to large-scale, multi-step processes.
Key Differences:
| Aspect | GitHub Actions | AWS CodePipeline |
| Structure | Job-based with parallelism | Stage-based, sequential execution |
| Parallelism | Supports matrix builds | Parallel actions within stages |
| Pipeline Flow | Flexible, conditional execution | Linear with artifact passing |
3.4 Execution Environment and Runtime
- GitHub Actions:
- Jobs run on ephemeral "runners" provided by GitHub, with support for Ubuntu, Windows, and macOS.
- For custom environments, self-hosted runners can be used, providing full control over the execution environment.
- Built-in support for dependency caching, helping to speed up build and test processes by reusing previous build results.
- AWS CodePipeline:
- Execution is delegated to specific AWS services:
- Source actions run within their respective services (e.g., S3, CodeCommit).
- Build actions typically occur within AWS CodeBuild.
- Deploy actions are executed using service-specific environments (e.g., CodeDeploy, Elastic Beanstalk).
- The configuration for each service’s environment must be defined separately within the respective AWS service.
- Execution is delegated to specific AWS services:
Key Differences:
| Aspect | GitHub Actions | AWS CodePipeline |
| Execution Environment | Ephemeral runners or self-hosted | AWS service-specific environments |
| Custom Environment Support | Full control with self-hosted runners | Limited to service-specific environments |
| Caching | Built-in caching for dependencies | Depends on the underlying service (e.g., CodeBuild) |
3.5 Deployment Capabilities
- GitHub Actions:
- Deployments are handled through environment-specific configurations and can include manual approval gates.
- The marketplace provides pre-built deployment actions that can be used for various environments, including AWS, Azure, Google Cloud, and more.
- Custom deployment scripts can be written within the workflow, providing flexibility for any deployment scenario.
- AWS CodePipeline:
- Native integration with AWS deployment services like CodeDeploy, which supports advanced deployment patterns like blue-green and canary deployments.
- CloudFormation can be used for automated infrastructure deployment alongside application code.
- Built-in rollback capabilities based on monitoring from CloudWatch or other services, ensuring smooth recovery during deployment failures.
Key Differences:
| Aspect | GitHub Actions | AWS CodePipeline |
| Deployment Integration | Flexible through marketplace actions | Deep integration with AWS services |
| Deployment Patterns | Custom scripting, manual gates | Native blue-green, canary, rollback |
| Infrastructure as Code | Custom scripts for deployment logic | CloudFormation for infrastructure |
4. Integration Ecosystem
The strength of a CI/CD platform often lies in how well it integrates with the tools, services, and workflows your team already uses. GitHub Actions and AWS CodePipeline both offer broad integration capabilities — but with very different philosophies. GitHub Actions leans into developer convenience and community-driven extensibility, while AWS CodePipeline focuses on deep integration with AWS services and enterprise-grade infrastructure.
4.1 GitHub Actions Marketplace and Custom Actions
GitHub Actions provides developers with a flexible and highly extensible automation environment, built natively into the GitHub platform.
Marketplace
The GitHub Actions Marketplace offers over 10,000 pre-built actions, covering:
- Testing (e.g., Jest, Cypress)
- Linting & formatting (e.g., ESLint, Prettier)
- Deployment (e.g., to AWS, Azure, Netlify, Vercel)
- Security (e.g., CodeQL, Snyk)
- Notifications (e.g., Slack, Microsoft Teams)
Using these pre-built actions often requires just a few lines in your workflow YAML:
| yaml - name: Upload to S3 uses: jakejarvis/s3-sync-action@master with: args: --acl public-read env: AWS_S3_BUCKET: ${{ secrets.AWS_S3_BUCKET }} AWS_ACCESS_KEY_ID: ${{ secrets.AWS_ACCESS_KEY_ID }} AWS_SECRET_ACCESS_KEY: ${{ secrets.AWS_SECRET_ACCESS_KEY }} |
This makes setup quick and accessible, even for small teams.
Custom Actions
When existing Marketplace actions don’t meet your needs, GitHub lets you create your own:
- JavaScript actions: Run natively in the GitHub environment
- Docker actions: Useful for encapsulating dependencies or specific tools
- Composite actions: Combine multiple steps into a reusable block
These actions can be versioned, shared across projects, or published publicly.
Reusable Workflows
Larger teams often standardize CI/CD with reusable workflows. These allow you to define templates and call them across repositories, encouraging consistency:
| yaml jobs: deploy: uses: org/.github/.github/workflows/deploy.yml@main with: environment: production secrets: inherit |
Takeaway: GitHub Actions emphasizes speed, flexibility, and ease of use — making it ideal for development teams that value automation and iteration over infrastructure complexity.
4.2 AWS Services Integration with CodePipeline
AWS CodePipeline is purpose-built for orchestrating software delivery across AWS infrastructure. It integrates tightly with AWS services, making it a strong fit for teams already operating in the AWS ecosystem.
Native Integration with AWS
CodePipeline supports end-to-end delivery using AWS services across each stage:
| Stage | AWS Services |
| Source | CodeCommit, GitHub (via CodeStar), S3 |
| Build | CodeBuild |
| Deploy | CodeDeploy, ECS, EKS, Lambda, Beanstalk |
| Approvals | Manual approval actions, EventBridge triggers |
| Monitoring | CloudWatch, CloudTrail |
These integrations are often preconfigured, making it easy to build pipelines that span services without needing third-party tools.
Infrastructure as Code
Pipelines can be defined as code using CloudFormation or the AWS CDK, aligning with infrastructure-as-code best practices. This enables version-controlled, replicable pipeline configurations:
| yaml Resources: Pipeline: Type: AWS::CodePipeline::Pipeline Properties: RoleArn: arn:aws:iam::123456789012:role/PipelineRole ArtifactStore: Type: S3 Location: my-artifact-bucket |
This declarative style is especially helpful for managing pipelines across multiple environments (e.g., dev, staging, prod).
Role-Based Security
Access control is enforced through IAM roles and policies, allowing precise permissions for each pipeline stage. This supports secure automation in environments that require strong access governance or cross-account deployments.
Takeaway: CodePipeline is designed for scalable, secure software delivery within AWS. Its strength lies in how seamlessly it fits into existing AWS infrastructure and security models.
4.3 Third-party Tool Integration Capabilities
Both platforms support external tools, but the integration experience differs significantly.
| Feature | GitHub Actions | AWS CodePipeline |
| Plugin Ecosystem | 10,000+ Marketplace actions | AWS Partner integrations, Lambda-based extensions |
| Secrets Management | GitHub Secrets (repo/org/env-level) | AWS Secrets Manager, Parameter Store |
| Custom Integrations | JavaScript, Docker, or composite actions | Custom action types or Lambda functions |
| Notifications & Alerts | Slack, Teams, Discord (via Marketplace) | SNS, EventBridge, AWS Chatbot |
| Logging & Monitoring | Job-level logs, Annotations, GitHub API | CloudWatch, CloudTrail, CloudWatch Logs |
GitHub Actions
GitHub’s approach prioritizes ease of use and developer experience. Third-party integrations often work with minimal setup, and GitHub’s wide adoption ensures most popular tools already offer official or community-maintained actions.
AWS CodePipeline
AWS favors more tightly controlled integrations. It supports third-party tools via AWS Partner Network, Lambda functions, and custom actions, but these often require manual configuration, IAM policies, and deeper infrastructure knowledge.
Takeaway: GitHub Actions offers quicker, more developer-friendly integrations, while CodePipeline is better suited for teams with strict security, compliance, or infrastructure requirements.
5. Operational Considerations
When choosing between GitHub Actions and AWS CodePipeline, it’s important to look beyond just features and think about cost, security, scale, and how you’ll monitor things in production. Here's how they stack up.
5.1 Pricing Models and Cost Comparison
GitHub Actions follows a usage-based pricing model, where you’re charged based on how long your jobs run and which type of runner you're using (Linux, Windows, macOS). There’s also a generous free tier — especially for open-source projects.
GitHub Actions (Private Repos) Pricing Snapshot:
| Plan | Free Minutes | Linux ($/min) | Windows ($/min) | macOS ($/min) |
| Free | 2,000 | $0.008 | $0.016 | $0.08 |
| Team | 3,000 | $0.008 | $0.016 | $0.08 |
| Enterprise | 50,000 | $0.008 | $0.016 | $0.08 |
With self-hosted runners, you avoid compute charges entirely — you just manage the infra yourself.
AWS CodePipeline is a little different. The newer V2 model bills based on the time each action runs, starting at $0.002 per minute, and includes 100 free minutes per month. You’ll also likely use CodeBuild (for build/test steps), which adds a separate charge (around $0.005/minute depending on compute type).
If we estimate a typical 3-stage pipeline (source → build → deploy), running 200 times per month:
- GitHub Actions (Linux): ~2–3 mins per job = $3.20–$4.80
- AWS CodePipeline + CodeBuild: ~4–5 mins total = $1.60 (pipeline) + ~$4–6 (CodeBuild)
Bottom line: GitHub Actions is predictable and cheaper at smaller scales. AWS becomes more efficient when you’re deep into their ecosystem and already paying for services like S3, CloudWatch, and CodeBuild.
5.2 Security and Compliance Features
Both platforms offer strong security capabilities — but their approaches are different.
- GitHub Actions keeps it simple. You define secrets at the repo/org level, control access via GitHub’s permission model, and can use OIDC for secure cloud authentication without long-lived credentials.
- AWS CodePipeline, on the other hand, is built with enterprise compliance in mind. It uses IAM for granular access control, supports fine-grained secret management with AWS Secrets Manager and SSM Parameter Store, and logs everything via CloudTrail.
Here's a quick comparison:
| Feature | GitHub Actions | AWS CodePipeline |
| Permissions | GitHub repo/org roles | IAM policies and resource permissions |
| Secrets | Encrypted secrets per repo/org/env | Secrets Manager, Parameter Store |
| Auditing | GitHub audit log | AWS CloudTrail + Config |
| Compliance | SOC 2, ISO, GDPR | SOC, FedRAMP, HIPAA, ISO, and more |
If you're working in finance, healthcare, or any regulated industry, AWS will likely check more boxes for you. For most dev teams, GitHub’s built-in protections are more than enough — and easier to manage.
5.3 Performance and Scalability
Performance is rarely the first thing you think about — until your CI/CD pipelines start slowing teams down.
GitHub Actions scales horizontally, meaning you can run lots of jobs in parallel — especially with matrix builds. GitHub-hosted runners have default concurrency limits (e.g., 20 concurrent jobs), but you can scale up with self-hosted runners.
Example:
| yaml strategy: matrix: node: [14, 16] os: [ubuntu-latest, windows-latest] |
AWS CodePipeline is built to scale vertically and across AWS accounts. It works well when you have pipelines that need to span multiple environments or teams — and you want to control deployments per region or per account.
- CodePipeline supports parallel stage execution, cross-account roles, and even multi-region delivery.
- Scaling mostly depends on how you configure supporting services (like CodeBuild or Lambda).
If you’re a product team pushing daily builds, GitHub Actions is fast and flexible. If you're managing a platform or need global infrastructure-level pipelines, AWS is built for it.
5.4 Monitoring and Observability
Both platforms give you insight into your pipelines, but again — in very different ways.
- GitHub Actions shows logs per step right in the Actions tab. It’s great for devs — easy to read, easy to debug.
- AWS CodePipeline uses CloudWatch and CloudTrail, giving you centralized logs, metrics, and event tracking. Ideal for teams with dedicated ops/SRE functions.
Need alerts? GitHub supports webhooks and integrations with tools like Slack or PagerDuty. AWS gives you SNS notifications, EventBridge hooks, and deeper hooks into other AWS services.
If you need real-time debugging? GitHub wins. If you need centralized monitoring across your cloud stack? AWS is more powerful — if more complex.
6. Developer Experience
Developer experience is often the deciding factor — especially for small teams who need to move fast.
6.1 Learning Curve and Documentation
GitHub Actions is easier to pick up, especially for teams already using GitHub. A basic deployment workflow takes 10 minutes to set up.
| yaml on: push: branches: [main] jobs: deploy: runs-on: ubuntu-latest steps: - uses: actions/checkout@v3 - run: ./deploy.sh |
AWS CodePipeline has more moving parts — IAM roles, service integrations, infrastructure setup — which means a steeper learning curve. That said, AWS documentation is extensive, and once you’re set up, you can reuse configurations across teams.
6.2 Community Support and Resources
GitHub Actions has a huge community behind it, especially in open source. You get access to:
- 10,000+ pre-built actions on the GitHub Marketplace
- Countless tutorials, blog posts, and GitHub repos to learn from
- Rich discussions and Q&A on Stack Overflow, Reddit, and more
CodePipeline is backed by AWS’s official ecosystem — well-documented and supported, but less open-source community content in comparison. If you like to learn by doing (and copying from GitHub Gists), Actions is a better fit.
6.3 Local Development and Testing
One of GitHub Actions' biggest perks is the ability to run workflows locally using tools like act:
| bash act push --job test |
This makes it easy to test workflows before pushing to your repo.
AWS doesn’t offer native local testing. You can simulate steps using SAM CLI, CodeBuild locally, or mocked test environments, but there’s more setup and overhead involved.
6.4 Debugging Capabilities
Both platforms give you step-by-step logs, but GitHub’s interface is more streamlined and focused on developer workflows. You can even re-run failed jobs directly from the UI.
AWS CodePipeline integrates logs into CloudWatch, so you’ll get more visibility — especially for multi-stage, long-running pipelines — but it’s not as immediate.
If you're debugging simple tests or deployment issues, GitHub is quicker. For large-scale infrastructure pipelines, AWS offers better end-to-end traceability.
7. Enterprise Considerations
When scaling to enterprise-level operations, both GitHub Actions and AWS CodePipeline have their advantages and drawbacks. Let’s take a closer look at some key aspects relevant for large organizations.
7.1 Governance and Compliance Controls
In the enterprise environment, governance and compliance are crucial. Organizations need to ensure that their CI/CD workflows adhere to strict security and regulatory standards.
- GitHub Actions:
- Access Control: Managed via GitHub’s repository permissions. Users can be granted access to specific workflows, and GitHub offers branch protection rules to control who can trigger builds or deployments.
- Audit Logs: Available at the organization level, but the feature set is relatively basic compared to AWS.
- Compliance Certifications: GitHub Actions has certifications for SOC 2 Type 1, ISO 27001, and others, which is sufficient for many tech-focused companies but may lack the depth needed for industries like finance or healthcare.
- AWS CodePipeline:
- Access Control: Uses IAM roles to assign permissions at a very granular level (e.g., who can update pipeline configurations, deploy code, etc.).
- Audit Logs: Fully integrated with AWS CloudTrail, enabling detailed logging of all pipeline events and actions. This is crucial for compliance in regulated industries.
- Compliance Certifications: AWS provides extensive certifications, including FedRAMP, HIPAA, SOC 2 Type 2, PCI-DSS, and more. This makes CodePipeline a better choice for highly regulated industries.
| Feature | GitHub Actions | AWS CodePipeline |
| Access Control | Repository-based permissions | IAM roles and service policies |
| Audit Logs | Basic, at organization level | Detailed, integrated with CloudTrail |
| Compliance Certifications | SOC 2, ISO 27001 | FedRAMP, HIPAA, SOC 2, PCI-DSS |
7.2 Team Collaboration Features
Collaboration features are essential for ensuring that multiple team members can work efficiently on CI/CD pipelines, especially in large organizations.
- GitHub Actions:
- Forking & Pull Requests: GitHub Actions allows workflows to trigger automatically on pull requests or forked repositories, making collaboration seamless for open-source and team-based projects.
- Reviewers and Approval Gates: GitHub Actions supports environment protection rules that can enforce approval workflows. For instance, deployments to production can require manual approval.
- AWS CodePipeline:
- Cross-Account Collaboration: CodePipeline supports cross-account deployments, which allows teams in different AWS accounts to collaborate more effectively, a feature especially useful in larger, multi-team organizations.
- Approval Gates: CodePipeline has built-in manual approval actions that can be placed between pipeline stages, which is a useful feature for environments with stringent quality control measures.
| Feature | GitHub Actions | AWS CodePipeline |
| Collaboration | Pull Requests, Forks, GitHub Teams | Cross-account pipelines, approval gates |
| Review and Approval Workflows | Environment protection rules | Manual approval actions in pipeline stages |
7.3 Multi-environment Pipeline Management
Managing multiple environments (development, staging, production) can be complex in large projects. Both platforms offer ways to manage pipelines across these environments.
- GitHub Actions:
- Environment Variables: You can define different environment variables for various environments (e.g., development vs. production). GitHub supports environment secrets for sensitive data, like API keys.
- Matrix Builds: GitHub allows the use of matrix builds to deploy across multiple environments concurrently, reducing pipeline execution time and providing flexibility.
- AWS CodePipeline:
- Multiple Pipeline Stages: CodePipeline lets you define multiple stages for each environment (e.g., build, deploy, approve). This helps maintain a clear distinction between different stages of the lifecycle.
- Cross-Region Deployments: With AWS, it’s easy to deploy to multiple regions using AWS CodeDeploy or Elastic Beanstalk.
| Feature | GitHub Actions | AWS CodePipeline |
| Environment Management | Environment variables, matrix builds | Multiple pipeline stages, cross-region deployment |
| Sensitive Data Management | Environment secrets, GitHub secrets | AWS Secrets Manager, Parameter Store |
7.4 Migration Paths Between Platforms
Migrating between CI/CD platforms can be challenging, especially in large enterprises that have complex pipelines. Here’s how both platforms handle migration.
- GitHub Actions:
- Simpler Migration: Migrating from other Git-based CI systems (like Jenkins or Travis CI) is relatively simple since GitHub Actions integrates tightly with GitHub repositories.
- Portability: GitHub Actions workflows are defined in YAML files, making it easy to export and reuse configurations in different repositories.
- AWS CodePipeline:
- Tighter AWS Integration: Migrating from another platform (e.g., Jenkins, CircleCI) to AWS CodePipeline might require a bit more effort due to its tight integration with AWS services and CloudFormation templates.
- Infrastructure-as-Code: CodePipeline encourages defining pipelines as code, which can make migrations to or from AWS easier in the long run, provided your infrastructure is already codified using CloudFormation or Terraform.
| Feature | GitHub Actions | AWS CodePipeline |
| Migration Ease | Easier from Git-based CI systems | Requires more setup for non-AWS systems |
| Portability | YAML workflows, GitHub-native | CloudFormation templates, AWS-specific |
8. Use Case Analysis
Choosing the right CI/CD platform largely depends on your project’s needs, team structure, and existing infrastructure. Let’s break down some ideal scenarios for both GitHub Actions and AWS CodePipeline.
8.1 Ideal Scenarios for GitHub Actions
- Small to Medium Teams: If you’re working within GitHub’s ecosystem, GitHub Actions is an excellent choice. It’s lightweight, fast to set up, and deeply integrated with GitHub repositories.
- Open Source Projects: GitHub Actions shines in open-source development where visibility, collaboration, and integration with GitHub’s ecosystem (e.g., issues, pull requests) are critical.
- Custom Workflows: If your project requires customized CI/CD workflows that can integrate with other external tools (like testing services, Docker, etc.), GitHub Actions provides flexibility through custom actions and reusable workflows.
8.2 Ideal Scenarios for AWS CodePipeline
- Large Enterprises with AWS Infrastructure: For organizations already embedded in the AWS ecosystem, CodePipeline offers deep integration with other AWS services like CodeDeploy, CloudFormation, and Lambda.
- Regulated Industries: CodePipeline’s robust security and compliance certifications (e.g., HIPAA, SOC 2 Type 2) make it ideal for companies in highly regulated sectors like healthcare, finance, and government.
- Complex Deployment Pipelines: If you have multi-stage, cross-region, or multi-account workflows, CodePipeline provides a more structured approach with integrated deployment strategies like blue/green or canary releases.
8.3 Hybrid Implementation Patterns
In some cases, combining both platforms might make sense. For instance, you could use GitHub Actions for development and testing in your GitHub repositories, then hand off to AWS CodePipeline for production deployment and integration with AWS services. This hybrid approach leverages the strengths of both platforms and can be particularly useful for teams with a mix of cloud and on-premise infrastructure.
| Scenario | GitHub Actions | AWS CodePipeline |
| Small Teams & Open Source | Ideal for fast, flexible CI/CD | Less suitable due to overhead |
| Large Enterprises with AWS | Lightweight but lacks AWS integration | Deep AWS service integration |
| Complex Multi-region Deployments | Limited to custom scripts | Native support for cross-region deployments |
9. Decision Framework
When deciding between GitHub Actions and AWS CodePipeline, organizations must consider a variety of factors. The decision should be aligned with specific project needs, team structures, and long-term goals. This section provides a framework for making an informed decision.
9.1 Selection Criteria Based on Project Requirements
Choosing between GitHub Actions and AWS CodePipeline often depends on the specific requirements of your project. Here’s how you can evaluate the platforms based on different project needs:
- Project Complexity:
- GitHub Actions is ideal for smaller, simpler projects or open-source initiatives. It provides an easy setup and is great for small teams or individual developers who need fast CI/CD pipelines that integrate well with GitHub.
- AWS CodePipeline is more suitable for larger projects with complex workflows, particularly if the project is deeply integrated with AWS services or requires advanced deployment strategies like blue/green or canary releases.
- Integration Needs:
- If your project already relies heavily on AWS (e.g., using EC2, Lambda, or CodeDeploy), AWS CodePipeline would be the better fit due to its deep integration with AWS services.
- GitHub Actions shines when your project involves open-source software or requires integration with third-party tools that are commonly used in the development lifecycle.
- Team Collaboration:
- Smaller teams or individual developers looking for streamlined workflows will benefit from GitHub Actions.
- Larger organizations requiring cross-account deployments or advanced team management features may find AWS CodePipeline more fitting.
| Criteria | GitHub Actions | AWS CodePipeline |
| Project Complexity | Simple, fast to set up | Complex workflows, multiple stages |
| Integration Needs | Best for GitHub-native tools | Deep AWS service integration |
| Team Collaboration | Great for smaller teams | Best for larger teams, cross-account support |
9.2 Avoiding Vendor Lock-in Considerations
One significant factor to keep in mind is avoiding vendor lock-in, which can limit flexibility and make it challenging to switch platforms in the future.
- GitHub Actions:
- GitHub-native: While highly integrated into the GitHub ecosystem, the dependency on GitHub as the source code management platform does present a degree of vendor lock-in. However, GitHub Actions can integrate with external services (e.g., Docker, Kubernetes, Azure, GCP, etc.), which provides some flexibility.
- If you plan to work across various cloud providers or non-AWS services, GitHub Actions' integration with multiple cloud environments reduces the risk of lock-in.
- AWS CodePipeline:
- AWS-centric: CodePipeline is deeply tied to the AWS ecosystem, which means heavy reliance on AWS infrastructure. This can lock you into AWS services and pricing models.
- However, AWS CodePipeline can also work with external services (e.g., GitHub, Bitbucket), but the overall experience is optimized for AWS, making it less flexible compared to GitHub Actions when migrating to or from other cloud providers.
| Feature | GitHub Actions | AWS CodePipeline |
| Vendor Lock-in Risk | Low (multi-cloud integration) | High (AWS-centric) |
| Flexibility in Cloud Providers | High (supports other providers) | Limited to AWS |
9.3 Long-term Strategic Alignment
As organizations scale and their needs evolve, it’s important to ensure that the chosen platform aligns with their long-term goals:
- GitHub Actions:
- Open-Source and Developer-Focused: GitHub Actions is highly suited for organizations looking to support open-source communities or stay within the GitHub ecosystem for simplicity and developer collaboration.
- GitHub’s frequent updates and evolving ecosystem ensure that it remains relevant in an ever-changing landscape. If your organization values developer-centric workflows and rapid innovation, GitHub Actions will likely align well with long-term objectives.
- AWS CodePipeline:
- Enterprise-Grade and AWS-Centric: AWS CodePipeline is ideal for companies that plan to expand their cloud infrastructure with AWS. Its integration with a vast range of AWS services means that CodePipeline is well-positioned for enterprise-scale projects that demand robust security, scalability, and reliability.
As AWS continues to grow and expand its services, CodePipeline will likely maintain its strong enterprise orientation. It’s a good choice for businesses focusing on cloud-native solutions and long-term cloud adoption.
| Criteria | GitHub Actions | AWS CodePipeline |
| Long-term Fit | Developer-focused, flexible | Enterprise-grade, AWS-centric |
| Cloud Integration | Multi-cloud, GitHub-native | AWS infrastructure, deep services |
10. Future Outlook
The CI/CD landscape continues to evolve, and both GitHub Actions and AWS CodePipeline are adapting to new trends and emerging technologies. This section outlines key trends and the future direction for both platforms.
10.1 Roadmap and Innovation Trends
- GitHub Actions:
GitHub Actions will focus on increasing third-party integrations, enhancing automation features, and potentially integrating AI-based code suggestions for more efficient workflows. - AWS CodePipeline:
AWS CodePipeline is expected to enhance AI capabilities, integrate machine learning for smarter automation, and improve hybrid and multi-cloud support for a more flexible CI/CD experience.
| Feature | GitHub Actions | AWS CodePipeline |
| Automation and AI | Enhanced DevOps automation | Smarter workflows with AI |
| Cloud Support | Multi-cloud integration | AWS-focused, expanding hybrid support |
10.2 Industry Direction in CI/CD
- Security: Expect stronger security automation in both platforms, with tools for DevSecOps becoming more integrated into workflows.
- Cloud-Native: Both platforms are adapting to containers and Kubernetes, with GitHub Actions focusing on container workflows and AWS expanding its EKS and ECS integrations.
| Trend | GitHub Actions | AWS CodePipeline |
| Security in CI/CD | Increased security checks | Built-in security features |
| Cloud-Native Focus | Support for Kubernetes, containers | Deeper integration with EKS, ECS |
10.3 Adapting to Evolving Development Practices
- GitHub Actions:
GitHub will continue to focus on collaboration, making it easy for distributed teams and open-source projects to work together. - AWS CodePipeline:
AWS will refine its offerings to better support cloud-native architectures and provide more customizable pipelines through Lambda and Step Functions.
| Trend | GitHub Actions | AWS CodePipeline |
| Collaboration Focus | Team-based, open-source workflows | Enterprise-level, cross-account |
| Developer Experience | Developer-friendly automation | Cloud-native, customizable |