1. Introduction
1.1 What is Cloud Identity Governance?
Cloud Identity Governance is the discipline of controlling and monitoring who has access to what within cloud environments. It goes beyond basic Identity and Access Management (IAM) by introducing oversight, policy enforcement, and lifecycle management for digital identities and roles across an organization’s cloud footprint.
In essence, it’s about ensuring that the right people have the right access to the right resources at the right time—and for the right reasons. In cloud environments like AWS and Azure, this means managing not just human users but also machine identities, service principals, and roles that automate infrastructure and application behavior.
1.2 Why Identity Governance Matters in the Cloud
Traditional security models focused on securing the network perimeter. But in the cloud, identity is the new perimeter. When a compromised identity can grant access to sensitive data, critical workloads, or production environments, identity governance becomes a first-line defense against breaches and compliance failures.
Poor identity governance can lead to excessive privileges, orphaned accounts, and unmonitored role escalation—all of which are prime targets for attackers. At the same time, businesses must ensure that users can still perform their tasks efficiently. Identity governance addresses this balance by introducing policy-driven, auditable controls that reduce risk without disrupting operations.
1.3 Overview of Azure AD and AWS IAM
Microsoft Azure and Amazon Web Services approach identity management in different ways, but both provide extensive tooling to manage authentication, authorization, and governance.
- Azure Active Directory (Azure AD) is the backbone of identity in Microsoft’s cloud. It supports user authentication, application access, role assignments, and more. Azure AD integrates tightly with Microsoft 365 and other SaaS platforms, making it ideal for hybrid cloud and enterprise scenarios.
- AWS Identity and Access Management (IAM) is AWS’s native solution for managing permissions across its services. IAM uses roles, users, groups, and policies to define what actions are allowed and under what conditions. AWS also provides tools like IAM Access Analyzer and AWS Organizations for broader governance.
Together, these platforms provide powerful but complex systems that require deliberate governance to avoid misconfigurations and security oversights.
1.4 Challenges in Multi-Cloud Identity Management
In single-cloud environments, identity governance is already a challenge. But as more organizations adopt a multi-cloud strategy, the complexity multiplies. Each cloud provider has its own identity model, terminology, and tooling. Synchronizing roles, policies, and user lifecycles across platforms is far from trivial.
Common challenges include:
- Inconsistent policy enforcement across clouds
- Redundant or misaligned identities
- Gaps in audit trails and visibility
- Difficulty implementing centralized access reviews and certifications
Without a unified strategy, organizations risk fragmented governance that can lead to security blind spots and compliance violations.
2. Core Principles of Identity Governance
2.1 Least Privilege Access
At the heart of identity governance is the principle of least privilege—users and services should only have the minimum access necessary to perform their functions. In cloud environments, this involves precisely scoping IAM policies, avoiding wildcard permissions, and ensuring that no one retains long-term administrative access unnecessarily.
Implementing least privilege effectively means continuously reviewing permissions, understanding access patterns, and removing excess rights as soon as they’re no longer needed. It’s not just a best practice; it’s a foundational requirement for cloud security.
2.2 Separation of Duties
Another key principle is separation of duties (SoD). This concept ensures that critical tasks are not fully controlled by a single individual or system, reducing the risk of abuse, fraud, or accidental damage. For example, a developer who writes code shouldn’t have the ability to deploy it directly into production without review.
In cloud environments, enforcing SoD means using role-based controls, approval workflows, and access reviews. It also requires architectural decisions—such as using different accounts or resource groups for development and production—to physically separate responsibilities and reduce the blast radius of any one user’s actions.
2.3 Just-In-Time Access and Time-Bound Roles
Standing access to sensitive resources is risky. Just-In-Time (JIT) access reduces this risk by allowing users to request elevated privileges only when needed, and only for a limited time. After that, permissions are revoked automatically.
Platforms like Azure AD Privileged Identity Management (PIM) and AWS IAM role chaining with session policies enable time-limited access with approval workflows and detailed logging. JIT models significantly reduce the window of opportunity for abuse or compromise, especially for administrative roles.
Adopting these principles—least privilege, separation of duties, and time-bound access—isn’t just about compliance. It’s about building a system that assumes failure is possible and minimizes its potential impact.
3. Identity and Access Management in Azure
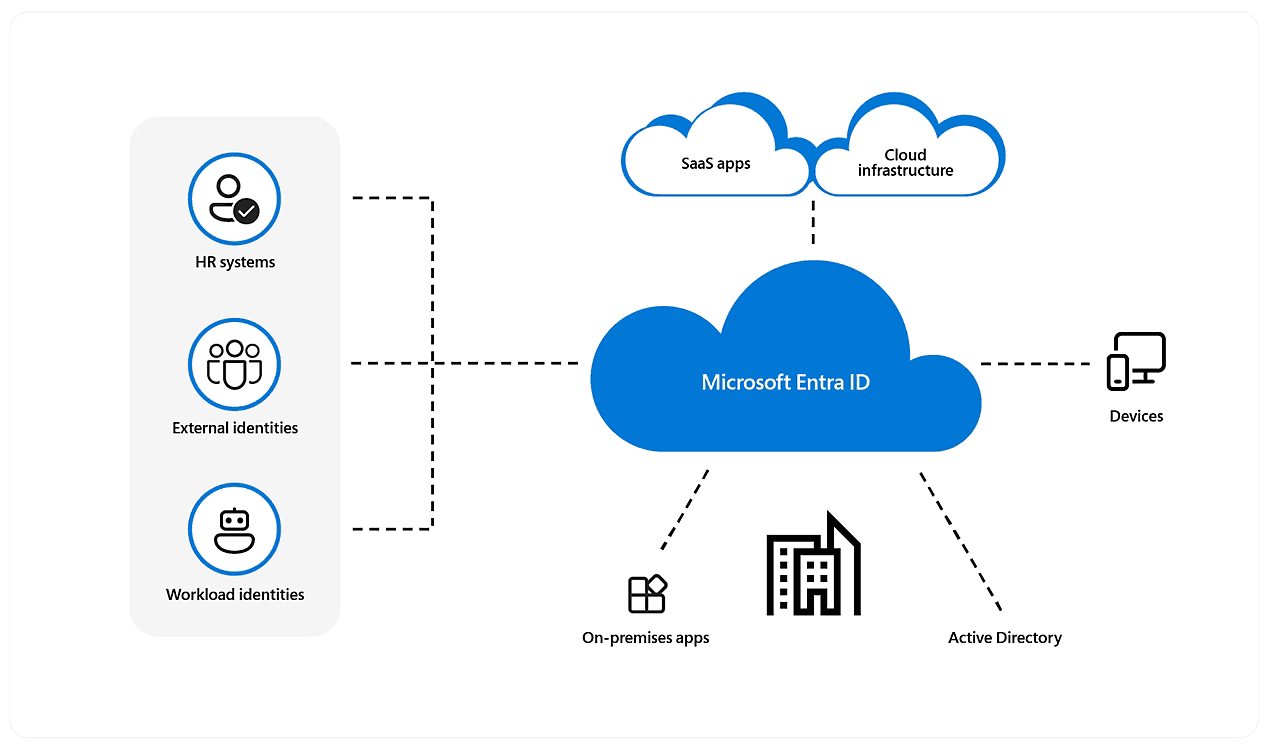
Source - Azure
3.1 Role-Based Access Control (RBAC) in Azure
Azure implements Role-Based Access Control (RBAC) to manage who can access resources and what actions they can perform. RBAC operates on four key components: security principals (users/groups/service identities), roles, scopes (resource levels), and permissions.
RBAC in Azure is hierarchical, allowing roles to be assigned at the subscription, resource group, or individual resource level. This flexibility is powerful—but it also makes proper scoping essential. Misconfigured roles can easily lead to over-privileged access or unauthorized modifications.
Organizations should aim to use built-in roles where possible and carefully design custom roles only when necessary. Most importantly, roles should be reviewed regularly to ensure they align with the current responsibilities of each user or service.
3.2 Conditional Access Policies
Azure AD’s Conditional Access is a dynamic policy engine that evaluates signals like user identity, location, device health, and app sensitivity before granting access. This allows organizations to go beyond static role assignments and implement context-aware controls.
For example, a user may be allowed to access an application only from a corporate device and during business hours. If they attempt access from an unknown IP or a jailbroken device, access can be denied or additional verification like multi-factor authentication (MFA) can be triggered.
Conditional Access is essential in modern zero-trust architectures, helping ensure that access decisions are based on risk rather than just identity alone.
3.3 Azure AD Privileged Identity Management (PIM)
Privileged Identity Management (PIM) is Azure’s built-in solution for managing, auditing, and controlling elevated access. It allows organizations to enforce JIT access for roles like Global Administrator or Security Reader, reducing the amount of time privileged roles are active.
With PIM, users must request access when needed, optionally providing a justification. Access can require approval and be subject to automatic timeouts. PIM also logs every activation, making it easy to audit administrative activity.
By minimizing the use of permanent admin rights and adding layers of control around elevated roles, PIM strengthens Azure’s defense against insider threats and compromised accounts.
4. Identity and Access Management in AWS
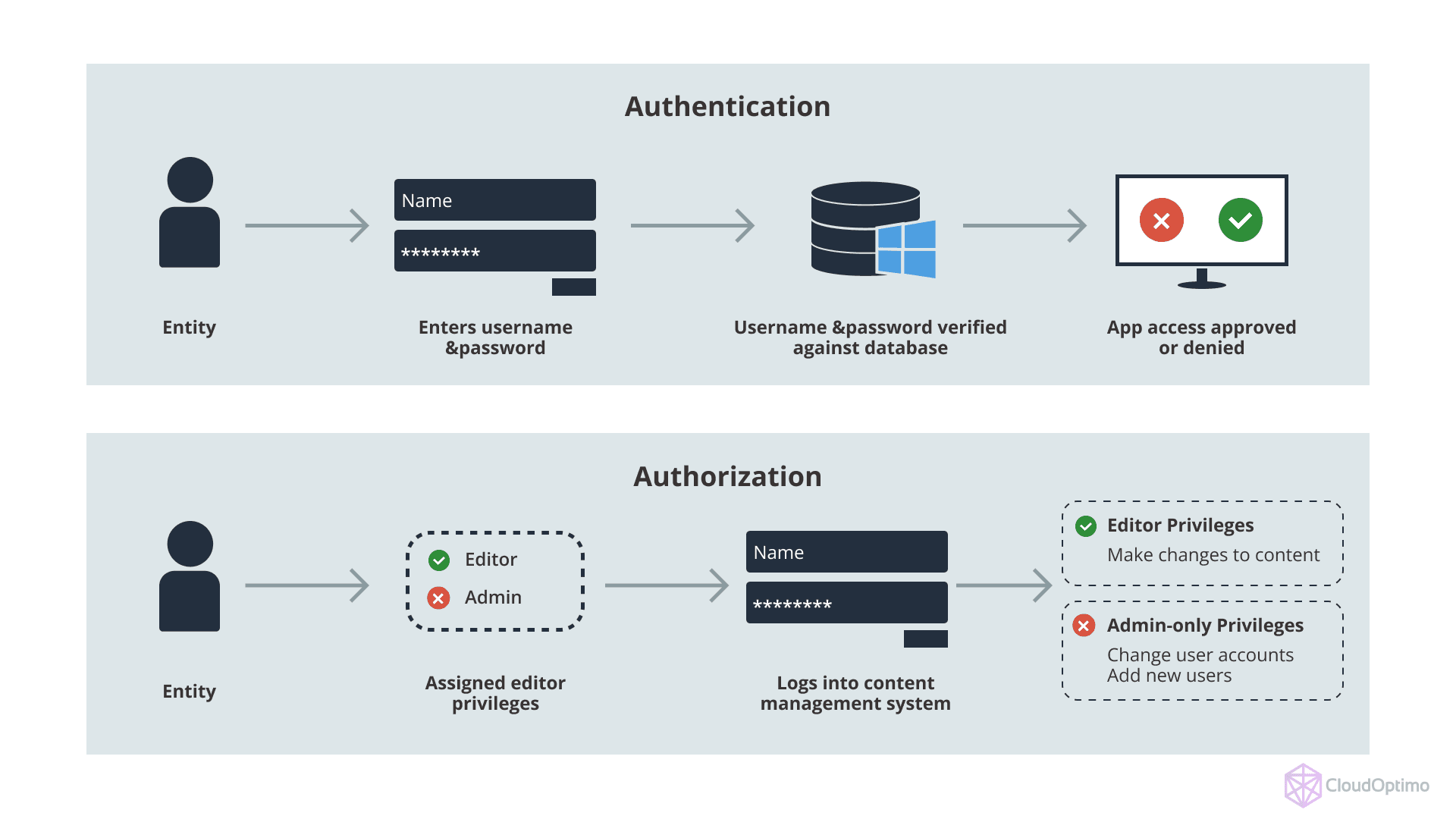
4.1 IAM Roles, Policies, and Permissions
At the core of AWS identity management is IAM (Identity and Access Management), which governs access through policies attached to roles, users, or groups. Permissions in AWS are explicitly granted via JSON-based policies, which define what actions are allowed (or denied), on which resources, and under what conditions.
The use of IAM roles—especially for EC2 instances, Lambda functions, and other AWS services—enables temporary and scoped access without hardcoded credentials. But without strict policy management, it's easy to create overly broad permissions that violate the principle of least privilege.
Best practice is to assign roles to workloads, not users, and to regularly audit permissions with tools like IAM Access Analyzer.
4.2 AWS Organizations and SCPs
For organizations managing multiple AWS accounts, AWS Organizations is a vital governance layer. It allows administrators to group accounts into Organizational Units (OUs) and apply Service Control Policies (SCPs) that act as permission guardrails.
SCPs don't grant permissions themselves; they limit what permissions can be granted within accounts. This ensures that even if an account admin mistakenly assigns a risky policy, the SCP can block its effect.
Example:
| Scenario | IAM Policy Allows | SCP Denies | Result |
| User tries to delete a bucket | Yes | No | Allowed |
| User tries to delete KMS keys | Yes | Yes | Blocked |
This layered approach significantly reduces the blast radius of misconfigurations.
4.3 AWS Identity Center (formerly SSO)
AWS Identity Center (previously AWS SSO) provides a centralized way to manage workforce access across AWS accounts and applications. It supports federation with external identity providers like Azure AD or Okta, making it ideal for hybrid environments.
Admins can assign users to roles in multiple accounts from a single console, streamlining access management. Identity Center also improves auditability, as it centralizes authentication and can enforce policies like MFA or session timeouts.
5. Cross-Cloud Identity Governance Strategies
5.1 Federation and SSO Between AWS and Azure
In multi-cloud setups, identity federation becomes a bridge between environments. Organizations often use a primary identity provider—such as Azure AD—to authenticate users across both AWS and Azure. This reduces identity sprawl and maintains a single source of truth for users and groups.
Through protocols like SAML and OIDC, users can authenticate once and access resources across clouds using assumed roles or enterprise applications, maintaining a seamless and secure user experience.
5.2 Centralized Identity Monitoring
Managing access across cloud providers is only half the challenge—monitoring and visibility are just as critical. Without centralized oversight, tracking access patterns or identifying anomalies becomes nearly impossible.
Modern organizations integrate identity telemetry from both AWS and Azure into a single monitoring layer, whether that’s via a SIEM, identity governance platform, or native integrations. This enables unified reporting, alerting, and compliance tracking.
5.3 Managing Shadow Identities in Multi-Cloud
Shadow identities—untracked service accounts, leftover test roles, or unregistered applications—are a growing problem in multi-cloud environments. Because each platform creates identities differently, it’s easy for orphaned or duplicate identities to go unnoticed.
To address this, organizations need to:
- Regularly scan both clouds for inactive or unused roles
- Consolidate identities where possible
- Decommission stale accounts using automated workflows
Governance tools should reconcile cloud-specific identities against a central directory to avoid fragmentation and minimize risk.
6. Role Lifecycle Management
6.1 Provisioning and Deprovisioning Users
Identity governance isn't just about controlling access—it’s about managing it through the full identity lifecycle. Provisioning should be driven by role-based models, with users automatically granted the access they need based on their team, function, or location.
Just as important is timely deprovisioning. When employees leave, change departments, or complete temporary projects, their access must be revoked immediately to reduce exposure.
6.2 Role Expiration and Review Cycles
Access should never be forever. Assigning expiration dates to temporary roles or project-based permissions reduces long-term risk. Azure AD and AWS both support ways to implement this—Azure via PIM, AWS via role session policies or third-party governance layers.
Regular access reviews ensure that users still require the roles they've been assigned. These reviews should involve resource owners, not just IT, to ensure business relevance.
6.3 Automating Access Reviews and Certifications
Manually conducting reviews and audits at scale doesn’t work. Automation is key. Most governance platforms now support scheduled access certifications, sending periodic alerts to managers or system owners to approve or revoke permissions.
An effective system includes:
- Automated alerts for unused access
- Integrated certification workflows
- Escalation paths for unreviewed items
When done right, this process both tightens security and reduces admin burden.
7. Monitoring and Auditing Identity Activity
7.1 Identity Logging in AWS CloudTrail and Azure Monitor
Both AWS and Azure offer comprehensive logging tools for identity-related events:
- AWS CloudTrail records every API call, including those related to identity actions like role assumption or policy changes.
- Azure Monitor and Azure AD logs capture sign-in events, access token usage, and conditional access outcomes.
These logs form the backbone of audit trails and incident response in identity governance.
7.2 Detecting Anomalous Access Patterns
Even with logging in place, the challenge lies in detecting abnormal behavior. Unusual sign-ins, unexpected privilege elevation, or rare combinations of actions can indicate a compromised identity or insider misuse.
Using tools with behavioral analytics—either built into Azure Sentinel or AWS GuardDuty—or external threat detection platforms helps surface anomalies early.
7.3 Integrating SIEM for Unified Identity Visibility
Most mature organizations forward logs to a centralized Security Information and Event Management (SIEM) system. This allows teams to correlate events across clouds, track activity over time, and generate alerts when identity rules are violated.
By aggregating data from CloudTrail, Azure Monitor, Identity Center, and other sources, a SIEM becomes the command center for identity observability, helping detect threats and demonstrate compliance at the same time.
8. Policy Enforcement and Guardrails
8.1 Using Azure Blueprints and AWS Service Control Policies
To enforce governance at scale, cloud providers offer policy management frameworks that act as guardrails—ensuring infrastructure and identities remain compliant by default.
- Azure Blueprints let organizations define and apply sets of governance controls—such as RBAC assignments, policy definitions, and resource templates—at the subscription level. This enables consistent deployments that are pre-wired for security.
- AWS Service Control Policies (SCPs) restrict what permissions can be granted within accounts under an AWS Organization. For example, even if a user tries to assign broad admin rights, an SCP can override it and block high-risk actions.
These tools ensure that no matter how teams operate within individual accounts or subscriptions, enterprise-wide constraints stay intact.
8.2 Enforcing Identity Hygiene at Scale
Maintaining identity hygiene means keeping your environment free of misconfigured, unused, or excessive access. But doing this manually in large, cloud-native environments is impractical.
To scale identity hygiene enforcement:
- Enforce naming conventions and tagging for traceability
- Set up expiration policies for temporary or project-based roles
- Use automated compliance scans to flag violations (e.g., inactive users with active credentials)
- Apply access guardrails with native tools like Azure Policy or AWS Config Rules
This ensures the identity layer remains lean, auditable, and defensible—especially during audits or incident response.
8.3 Policy-as-Code for Governance Automation
Modern governance doesn't stop at manual reviews. With Policy-as-Code (PaC), teams can define access rules, security controls, and compliance requirements in version-controlled templates.
Using tools like:
- Azure Policy + Bicep/ARM templates
- AWS CloudFormation + SCPs or custom Config Rules
- Open-source frameworks like Open Policy Agent (OPA)
You can automate enforcement, testing, and deployment of identity governance rules. PaC turns governance into part of the development pipeline, reducing drift and improving security consistency across environments.
9. Common Identity Governance Pitfalls
9.1 Overprovisioned Accounts and Role Creep
A frequent governance failure is overprovisioning—users and services having far more access than necessary. This often happens due to vague role definitions, shortcuts during urgent tasks, or lack of periodic reviews.
Over time, users accumulate permissions they no longer need, a phenomenon known as role creep. In the event of a breach or insider threat, these excessive privileges can become dangerous.
The solution? Enforce least privilege by default and implement regular access reviews with owner validation.
9.2 Unused Roles and Orphaned Identities
Cloud environments accumulate clutter quickly. Test roles, service accounts from deprecated apps, or contractor identities often stick around long after they’re needed.
These orphaned identities represent unmonitored entry points and should be treated as risks. If they’re not assigned, rotated, or monitored, they can be exploited quietly.
Implementing automated deprovisioning and usage-based audits (e.g., last login, last assumed role) is essential to prevent identity sprawl.
9.3 Weak MFA and Poor Credential Hygiene
Despite the push toward stronger identity controls, many environments still allow console access without MFA, or use outdated authentication methods like static keys and passwords.
Poor credential hygiene includes:
- Reusing secrets across environments
- Storing keys in code or shared folders
- Not rotating access tokens or keys regularly
Both Azure and AWS offer native enforcement mechanisms to mandate MFA, rotate keys, and integrate passwordless or biometric authentication. Failing to use them is one of the most easily avoidable mistakes.
10. Best Practices Checklist and Governance Maturity
10.1 Building a Cloud Identity Governance Roadmap
Identity governance is not a one-time project—it’s a continuous journey. A good starting point is building a roadmap that outlines short-term fixes and long-term goals.
Your roadmap should include:
- Inventory of all active identities (users, services, apps)
- Current state of access reviews and provisioning processes
- Governance tools in use and gaps identified
- Plans to centralize identity management across platforms
A phased approach helps avoid burnout while driving meaningful progress.
10.2 Aligning with Compliance Frameworks
Cloud identity governance must align with regulatory and industry frameworks like:
- ISO 27001: Identity lifecycle and access review standards
- SOC 2: Role management and auditability
- HIPAA/GDPR: User data access and retention controls
Most frameworks require proof of access controls, logging, and periodic reviews. Building compliance into your identity governance model makes audits smoother and more predictable.
10.3 Continuous Improvement and Governance Maturity Models
Mature governance isn’t just about tools—it’s about process, culture, and automation. Organizations should move from reactive, manual processes to automated, policy-driven governance.
A simplified governance maturity curve might look like:
| Stage | Characteristics |
| Ad-hoc | Manual provisioning, no audits, no MFA |
| Basic | Role-based access, minimal reviews, some logging |
| Managed | Scheduled audits, centralized identity, MFA enforced |
| Optimized | Automated reviews, policy-as-code, cross-cloud integration |
Climbing this curve not only improves security but also simplifies operations, reduces friction, and prepares your organization for scale.
11. Conclusion
In a cloud-first world, identity is the control plane that connects users, services, and infrastructure. Whether you're operating in Azure, AWS, or both, strong identity governance is essential to securing your environment, meeting compliance standards, and minimizing operational risk.
From least privilege and role lifecycle management to automation through Policy-as-Code, effective governance is not just about preventing misuse—it's about enabling secure access at scale. The path forward involves continuous auditing, cross-cloud visibility, and embedding identity into your DevSecOps strategy.
Identity is not just a technical concern; it's a strategic asset. The organizations that govern it wisely will move faster, stay safer, and scale smarter.