The Rise of Multi-Cloud and What It Means for Security
The growing adoption of multi-cloud strategies introduces new challenges in managing cloud security. Each cloud brings its architecture, terminology, and security model. Managing identity, enforcing policies, and protecting data becomes more complex, not because the principles change, but because the implementations do.
You must first understand the shared foundation to create an effective security strategy across cloud platforms. Regardless of provider, every security model rests on three core pillars: Identity and Access Management (IAM), Policy Enforcement, and Encryption. These are the controls that define who can access what, under what conditions, and how data is protected at all times.
Shared Goals, Different Implementations
Across AWS, Azure, and GCP, the core objectives of cloud security remain consistent:
- Controlling access: Who can do what, and under which conditions
- Enforcing rules: Defining boundaries around users, data, and services
- Protecting data: Ensuring information is safe both in storage and in transit
These objectives are met through three critical components — present in every cloud, but realized differently:
- Identity and Access Management (IAM): The structure that defines and manages identities and permissions
- Policies: The logic layer that determines what actions are allowed or denied
- Encryption: The mechanism that secures data, even if access controls fail
Understanding these building blocks is essential before comparing how each provider implements them. Without a solid foundation, the complexities of AWS, Azure, and GCP may seem unnecessarily complicated.
Understanding the Building Blocks: IAM, Policy, and Encryption
Before discussing platform-specific details, let's establish a common understanding of the three pillars of cloud security. These are the foundation of any secure cloud environment.
IAM – Controlling Access
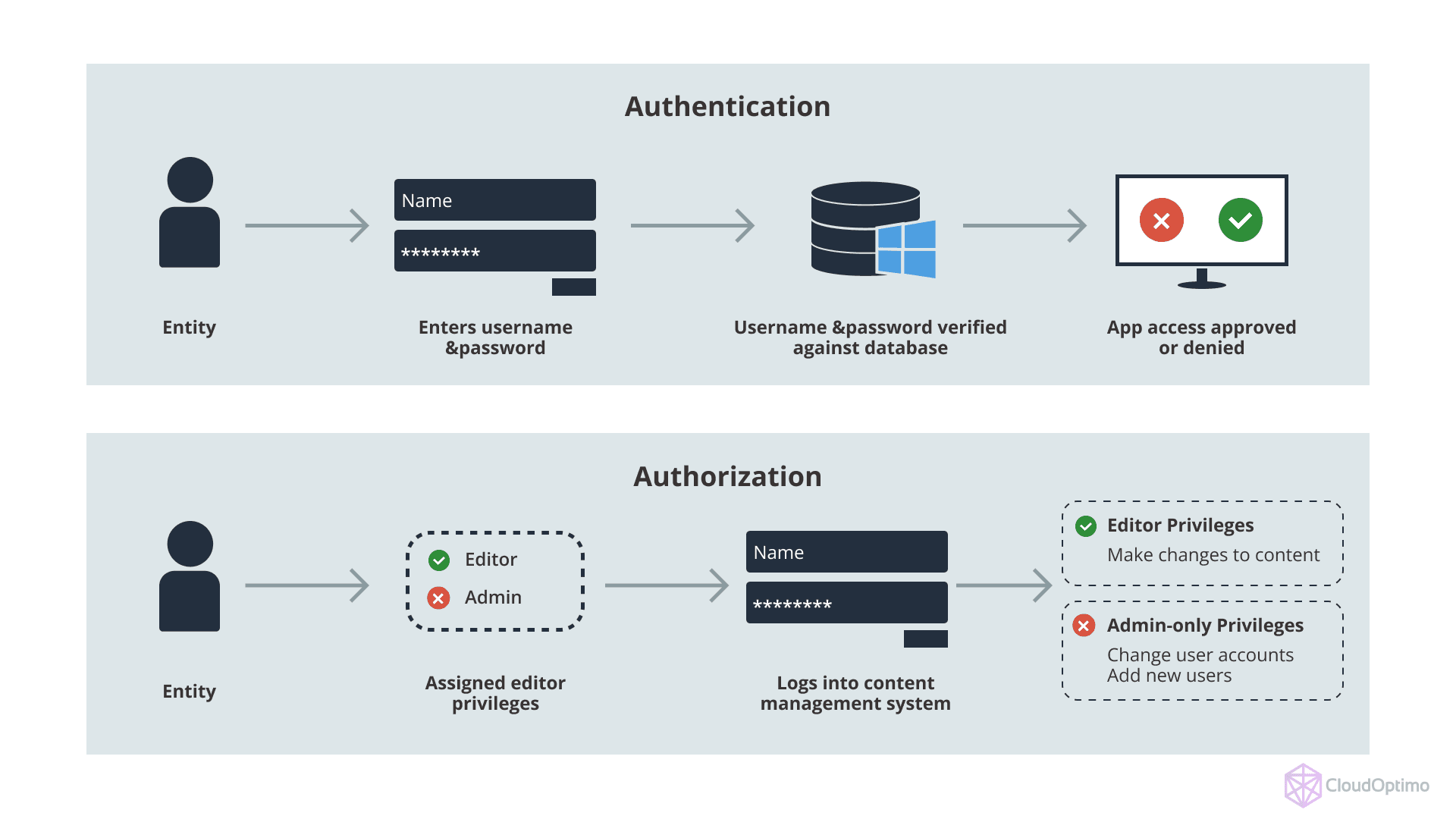
IAM governs who has access to cloud resources and what actions they are permitted to perform. It encompasses:
- Identities – Users, services, and applications that require access
- Authentication – Verifying the legitimacy of those identities
- Authorization – Determining access rights based on predefined roles or permissions
Each cloud platform implements IAM in its own way, but the core objective remains consistent: making sure access is given safely, on purpose, and can be tracked.
Policies – Enforcing Security Rules
Policies define how access is granted or denied, specify the conditions under which resources can be used, and serve as the enforcement mechanism for security controls.
Typical policy rules address:
- What operations can be performed on specific resources
- When and under what conditions is access allowed
- Restrictions based on attributes like IP address, user identity, or service context
The complexity and flexibility of policy models vary across platforms, but their purpose is universal: to implement intent and ensure consistent enforcement.
Encryption: Safeguarding Data Integrity and Confidentiality
Encryption ensures that even if unauthorized access occurs, the data remains unreadable without proper decryption keys. Cloud encryption typically applies in two primary contexts:
- At Rest – Encrypting data stored on disks, databases, and backups
- In Transit – Protecting data moving between systems or across networks
Cloud providers offer a range of encryption models, including platform-managed keys, customer-managed keys, and customer-supplied keys, each with distinct implications for control, compliance, and operational complexity.
Shared Responsibility Model: Defining Security Ownership
All major cloud providers operate under a shared responsibility model, which explains the division of security responsibilities between the provider and the customer.
Cloud Provider is responsible for:
- Physical security of data centers
- Network infrastructure and hardware
- Virtualization and foundational services
Customer is responsible for:
- Data security and integrity
- Application security and configuration
- Identity and Access Management (IAM)
- Policy definitions and enforcement
- Encryption key management and usage
Understanding this division is essential when designing secure cloud architectures and directly influences how IAM, policies, and encryption are implemented across platforms.
Comparison Snapshot: AWS vs Azure vs GCP
Before diving into specifics, here’s a high-level look at how the major cloud platforms compare. Each balances control, complexity, and ease differently, shaping how organizations approach IAM, policy enforcement, and encryption.
| Aspect | AWS | Azure | GCP |
| IAM Approach | Granular, flexible, complex | Enterprise-ready, RBAC-based | Simple, hierarchical, intuitive |
| Policy Model | Multi-layered, powerful | Dual system (RBAC + Policy) | Clean additive model |
| Encryption Defaults | Must be enabled for many services | Enabled by default | Enabled by default |
| Customer Key Options | Full spectrum (SSE, KMS, CSEK) | Key Vault with CMK and HSM | CMEK and CSEK via Cloud KMS |
| Ease of Use | Most powerful, most complex | Balanced and familiar | Easiest to adopt, cleanest design |
| Maturity | Most mature and feature-rich | Strong enterprise focus | Developer-centric, newer ecosystem |
| Multi-Cloud Fit | Rich 3rd-party support | Strong hybrid capabilities | Clean APIs, easy integration |
Let’s start with how each cloud provider structures identity and access, beginning with AWS’s detailed IAM model.
IAM Models: Identity & Access Across AWS, Azure, and GCP
Each major cloud provider offers a unique IAM framework shaped by its platform architecture and customer needs. Understanding these differences is key to designing secure, scalable, and manageable access controls in multi-cloud environments.
AWS IAM: Precision and Granularity at the Core
AWS IAM is like a finely detailed blueprint for access, built around users, groups, roles, and policies. It favors explicit relationships and granular permissions.
Flat but flexible architecture:
Unlike Azure or GCP, AWS IAM doesn’t organize permissions hierarchically. Instead, each user, group, or role gets policies attached directly. This means you must explicitly manage permissions for every entity, which can get complex in large organizations, but allows very detailed access specifications.
Temporary roles and delegation:
AWS’s use of roles supports dynamic scenarios, like EC2 instances assuming a role to access S3 buckets, or cross-account access between teams, increasing security by avoiding permanent credentials.
Policy Simulator & an Access Analyzer
AWS provides tools like the Policy Simulator to test permissions before deployment and Access Analyzer to identify resources accessible from outside your account, helping prevent misconfigurations.
Real-World Impact:
For an organization with multiple teams needing different levels of access to hundreds of AWS resources, AWS IAM allows tailoring access per user or role down to specific API calls, ideal when tight control is essential. But this precision demands continuous management effort to avoid permission sprawl or conflicts.
This design suits organizations that want exacting control, especially when heavily invested in AWS services.
Azure IAM: Enterprise Familiarity with Layered Scope Control
Azure’s IAM system is built around Microsoft Entra ID (formerly Azure AD), bringing enterprise-grade identity management into the cloud. It mirrors traditional organizational structures while layering access through scopes.
Hierarchy and Scope-Aware Permissions:
Unlike AWS’s flat model, Azure IAM applies permissions at four levels: management group, subscription, resource group, and resource. Roles are assigned to security principals (users, groups, service principals, or managed identities) at a specific scope, giving admins a clear and scalable way to manage access as environments grow.
Role-Based Access Control (RBAC):
Azure offers a rich set of built-in roles like Contributor or Reader, and supports custom roles for finer control. Assigning roles at higher scopes trickles permissions down the hierarchy—ideal for centralized governance.
Conditional Access & Privileged Identity Management:
Azure excels in adaptive access control. Conditional Access enables context-aware policies (location, device, risk score), while PIM allows just-in-time access with approval workflows and audit logging for sensitive roles.
Real-World Impact:
For enterprises already using Microsoft ecosystems, Azure IAM offers a familiar model that extends naturally into cloud services. Teams can enforce broad policies at the subscription level, while still refining access at the resource level—balancing control and manageability with strong enterprise integration.
GCP IAM: Clean Hierarchy with Context-Aware Flexibility
Google Cloud IAM highlights simplicity with precision, leveraging a resource hierarchy and a binding model that cleanly maps members to roles at any level of the structure.
Hierarchical Resource Tree:
GCP organizes everything under a three-level model: Organization → Folder → Project, with individual resources living inside projects. Permissions flow downward, allowing roles to be granted broadly (at the org level) or narrowly (on a single resource).
Bindings Over Entities:
Rather than attaching policies to identities, GCP uses bindings that associate a member (user, group, service account) with a role on a resource. This results in clear, declarative access relationships that scale well with infrastructure.
IAM Conditions & Policy Intelligence:
GCP supports IAM Conditions—a powerful feature for setting time-based, IP-restricted, or attribute-aware permissions. Its Policy Intelligence suite suggests least-privilege adjustments and flags risky grants, promoting secure-by-default access.
Real-World Impact:
Organizations looking for a streamlined access model that still supports complex use cases will appreciate GCP’s logical structure. It’s particularly well-suited to cloud-native teams who prioritize clean role separation, automation, and policy transparency.
| Feature | AWS IAM | Azure IAM | GCP IAM |
| Architecture | Flat, explicit user/group/role policy model | Hierarchical scopes (Mgmt Group > Subscription > RG > Resource) | Resource hierarchy (Org > Folder > Project > Resource) |
| Access Control | Fine-grained JSON policies on users/groups/roles | Role assignments at scoped levels | Role bindings on members with optional conditions |
| Temporary Access | Roles with assumed identities | Privileged Identity Management with time-limited access | Service accounts with scoped permissions |
| Unique Strength | Detailed, granular permissions and policy tools | Enterprise integration & conditional access policies | Clear hierarchy and flexible, attribute-based conditions |
| Ideal For | AWS-centric environments need deep control | Organizations leveraging Microsoft’s ecosystem | Teams favoring simplicity with a scalable hierarchy |
Policy Enforcement: How Access Rules Are Applied in Practice
IAM defines who can access what, but policies determine how, when, and under what conditions that access is permitted. Each cloud provider implements policy enforcement differently, combining access control, governance, and organizational boundaries in distinct ways.
AWS: Multi-Layered Policies for Fine-Grained Control
AWS offers a powerful but complex policy model that spans identity-based, resource-based, and organization-wide controls, each evaluated independently but in concert.
Identity Policies:
Attached to users, groups, or roles, these define what actions an identity can perform across services. They are the primary mechanism for everyday access control.
Resource Policies:
Applied directly to services like S3, Lambda, or SNS. These specify who can interact with a specific resource, even across accounts.
Service Control Policies (SCPs):
Used in AWS Organizations to restrict what member accounts are allowed to do. They don’t grant permissions but set upper bounds—ideal for enforcing global restrictions like disallowing specific regions or services.
Policy Evaluation Logic:
AWS follows a layered evaluation model where implicit deny is the default. Permissions are allowed only when explicitly granted and not explicitly denied. SCPs act as final organizational boundaries that override any other permissions.
Real-World Impact:
AWS’s enforcement model provides ultimate flexibility and security isolation, especially for complex enterprises, but demands deep expertise in policy interplay and ongoing audit hygiene to avoid unintentional denials or privilege creep.
Azure: Dual Enforcement for Access and Governance
Azure separates policy enforcement into two clear domains: RBAC for permissions and Azure Policy for compliance and governance.
RBAC (Role-Based Access Control):
Defines what users or identities can do with resources. Roles can be assigned at multiple scopes (resource, resource group, subscription, management group).
Azure Policy:
Controls how resources are configured or deployed. For example, a policy might block creation of public IP addresses or enforce encryption standards across all storage accounts.
Management Groups:
Enable consistent policy enforcement across all subscriptions within an enterprise. Both RBAC and Azure Policy can be applied at this scope for centralized control.
Policy Evaluation Logic:
Azure independently evaluates RBAC (for permissions) and Azure Policy (for compliance). Both must pass for an action to succeed, meaning that a valid RBAC permission can still be blocked by a non-compliant policy.
Real-World Impact:
Azure’s clear separation between access and compliance aligns well with enterprise IT operations. Organizations gain strong governance capabilities without deeply intertwining them with day-to-day role assignments.
GCP: Declarative Policies with Organizational Guardrails
Google Cloud uses a declarative policy model where permissions cascade down its resource hierarchy and are filtered by high-level constraints.
IAM Policies:
These define what identities can do at various scopes - organization, folder, project, or individual resource. Policies are additive and inherit downward.
Organization Policies:
Centralized controls that apply constraints across projects or folders. These policies don’t manage identity access directly, but govern what’s allowed within a given scope (e.g., disallowing public IPs or limiting service usage to specific regions).
IAM Conditions & Constraints:
Add precision to role bindings, enabling conditional access rules based on attributes like request time, resource tags, or IP ranges.
Policy Evaluation Logic:
GCP starts from the most specific resource and works upward. Permissions are granted only if explicitly defined and not restricted by organization policies or IAM conditions.
Real-World Impact:
GCP’s policy model offers clarity and predictability, especially for cloud-native teams. It scales easily with folder/project structures and supports advanced constraints without excessive role complexity.
| Feature | AWS | Azure | GCP |
| Policy Types | Identity, Resource, SCPs | RBAC, Azure Policy | IAM Policies, Organization Policies |
| Governance Mechanism | SCPs restrict actions across org accounts | Azure Policy governs resource configuration | Org Policies constrain allowed behaviors across the hierarchy |
| Scope Granularity | Account-level to individual resource | Management group → Subscription → Resource group → Resource | Org → Folder → Project → Resource |
| Enforcement Separation | Access and org guardrails are evaluated together | RBAC (access) and Azure Policy (compliance) are evaluated separately | Unified evaluation from specific → general |
| Conditions & Constraints | Limited condition keys in IAM and resource policies | Conditional Access (via Entra ID), not deeply policy-integrated | IAM Conditions + Org Policy Constraints |
| Policy Evaluation | Layered: Explicit allow needed, deny overrides, SCP final | Dual-path: Both RBAC and Azure Policy must allow | Additive with restriction checks; least privilege enforced |
Encryption Models: Securing Data at Rest and In Transit
Encryption serves as the failsafe in cloud security. Even if access controls are compromised, strong encryption ensures that data remains unreadable without the right keys. While all major cloud platforms provide encryption by default, the depth of control, flexibility, and integration with services vary significantly across AWS, Azure, and GCP.
AWS: Granular Options with Deep KMS Integration
Amazon Web Services delivers a robust, multi-layered encryption model with fine-grained control through its Key Management Service (KMS) and multiple server-side encryption options.
Server-Side Encryption (SSE):
AWS offers multiple SSE options to match different security and control needs:
- SSE-S3 – Fully managed by AWS, ideal for simplicity.
- SSE-KMS – Uses AWS KMS, offering better visibility, audit logs, and control over key access.
- SSE-C – Customer provides the key for each request; AWS never stores the key, offering maximum isolation.
Key Hierarchy with KMS:
AWS KMS uses a two-tier approach:
- Customer Master Keys (CMKs) encrypt data keys, which then encrypt the actual data.
- This enables efficient key rotation and separation of duties between data access and key control.
Key Ownership:
- AWS-Managed Keys offer convenience with minimal configuration.
- Customer-Managed Keys allow fine control over usage, permissions, lifecycle, and deletion policies.
Encryption In Transit:
All AWS services support TLS/SSL, and customers can implement VPNs or Direct Connect for encrypted data transfer across networks.
Real-World Impact:
AWS is ideal for security-conscious organizations needing fine-tuned key policies, cross-service integration, and hardware-backed key storage, but this power comes with management overhead.
Azure: Encryption by Default with Enterprise-Grade Key Management
Microsoft Azure prioritizes default encryption across all services while enabling organizations to elevate control through Azure Key Vault and customer-managed keys.
Encryption Defaults:
Most Azure services encrypt data at rest automatically with Microsoft-managed keys, ensuring strong baseline protection without requiring action from users.
Customer-Managed Keys (CMKs):
Organizations can use Azure Key Vault to generate and manage their keys. This supports granular access policies, key rotation, and compliance needs.
Azure Key Vault Features:
- Central repository for keys, secrets, and certificates
- Supports HSM-backed keys for FIPS 140-2 Level 3 compliance
- Deep integration with RBAC, logging, and alerting
Encryption In Transit:
TLS is enforced across Azure services, and private endpoints or ExpressRoute can ensure encrypted communication between cloud and on-prem environments.
Real-World Impact:
Azure’s encryption model aligns with compliance-heavy enterprises looking for centralized governance, seamless Active Directory integration, and a secure-by-default baseline.
GCP: Declarative Key Control with Transparent Integration
Google Cloud Platform combines simplicity and flexibility with a strong focus on policy-based key management, driven by deep integration with Cloud KMS and scalable resource hierarchies.
Default Encryption:
All data at rest is encrypted using Google-managed keys by default, offering out-of-the-box security.
Customer-Managed Encryption Keys (CMEK):
Users can create, manage, and monitor their own keys using Cloud KMS, with options for automatic rotation, access control, and audit trails.
Customer-Supplied Encryption Keys (CSEK):
For maximum control, customers can supply their own keys during API calls. Google never stores these keys, enhancing privacy but requiring full key lifecycle management.
Cloud KMS Features:
- Seamless service integration (e.g., BigQuery, GCS, Compute Engine)
- IAM-based permissions on keys
- Support for HSM-protected keys
Encryption In Transit:
TLS is standard for all inter-service and client-service traffic. GCP also supports dedicated interconnects and VPC Service Controls to limit data movement.
Real-World Impact:
GCP strikes a balance between security automation and granular control, making it ideal for organizations focused on policy transparency and scalable encryption governance.
| Feature | AWS | Azure | GCP |
| Default Encryption | Yes, with AWS-managed keys | Yes, with Microsoft-managed keys | Yes, with Google-managed keys |
| Customer-Managed Keys (CMK) | Via AWS KMS, deeply integrated with access policies | Via Azure Key Vault with RBAC and HSM options | Via Cloud KMS, IAM-based access |
| Customer-Supplied Keys (CSK) | SSE-C supported for S3; key not stored by AWS | Not broadly supported | CSEK supported for select services; key never stored |
| Key Management Service | AWS KMS with key hierarchy and policy support | Azure Key Vault for keys, secrets, and certificates | Cloud KMS with IAM and audit integration |
| Key Rotation | Manual or automatic (for CMKs) | Supported via Key Vault automation | Supported; configurable per key |
| Encryption In Transit | TLS, VPN, Direct Connect | TLS, ExpressRoute, private endpoints | TLS, Dedicated Interconnect, VPC Service Controls |
| Audit & Logging | CloudTrail logs key usage, integrated with KMS | Integrated with Azure Monitor and Activity Logs | Cloud Audit Logs provide detailed visibility |
| Unique Strength | Fine-grained encryption control and diverse SSE modes | Enterprise integration and HSM-grade centralized management | Clean declarative model with transparent key management |
Real-Life Use Cases and Challenges in Multi-Cloud Security
While understanding the distinct implementations of IAM, policies, and encryption across AWS, Azure, and Google Cloud is critical, the real complexity emerges when organizations apply these controls in multi-cloud environments. Let’s explore practical scenarios where these issues commonly arise and how organizations have successfully addressed them.
Guidance for Security Architects
As a security architect working in a multi-cloud environment, your role extends beyond understanding individual platforms to creating cohesive security strategies that work across different cloud providers. Here's practical guidance for designing and implementing effective cross-cloud security.
Designing IAM with Multi-Cloud in Mind
Start with Business Roles, Not Technical Roles: Define roles based on business functions rather than technical permissions. A "Marketing Analyst" should have a consistent set of capabilities, whether they're working with data in AWS, Azure, or GCP. This business-first approach makes it easier to implement consistent permissions across platforms.
Implement Identity Federation Early: Choose a central identity provider and implement federation to all cloud platforms from the beginning. Popular options include:
- Azure Active Directory (Microsoft Entra ID) for organizations using Microsoft technologies
- Okta or Ping Identity for platform-agnostic solutions
- AWS IAM Identity Center for AWS-centric environments with multi-cloud needs
Plan for Service Accounts and Automation: Applications and automated processes need identities just like humans do. Design a consistent approach for managing service accounts across platforms:
- Use standardized naming conventions
- Implement automated credential rotation
- Monitor service account usage and permissions
- Plan for service account lifecycle management
Consider the Principle of Least Privilege at Scale: While least privilege is a fundamental security principle, implementing it across multiple cloud platforms requires careful planning:
- Start with minimal permissions and expand as needed
- Use time-limited access for sensitive operations
- Implement just-in-time access where possible
- Regular review and cleanup of unused permissions
Normalizing Policy Language and Enforcement
Create a Policy Translation Layer: Develop a common language for expressing security policies that can be translated into platform-specific implementations. This might involve:
- Creating a standard vocabulary for common actions (read, write, create, delete)
- Mapping business requirements to technical permissions
- Documenting platform-specific nuances and limitations
Implement Policy as Code: Treat security policies as code to ensure consistency and enable proper change management.
- Use version control for all policy definitions
- Implement automated testing of policy changes
- Create deployment pipelines that can update policies across multiple platforms
- Maintain rollback capabilities for policy changes
Standardize Policy Evaluation Patterns: While you can't change how each platform evaluates policies, you can standardize how your organization thinks about policy evaluation:
- Document the evaluation logic for each platform
- Create troubleshooting guides for common policy issues
- Implement consistent logging and monitoring across platforms
- Train teams on platform-specific policy behaviors
Plan for Policy Conflicts: When the same user or application has different permissions on different platforms, conflicts can arise:
- Document intentional differences and their business justification
- Implement monitoring to detect unexpected permission disparities
- Create processes for resolving cross-platform access issues
- Consider implementing compensating controls when platforms can't provide equivalent functionality
Choosing the Right Encryption Approach per Use Case
Assess Your Compliance Requirements First: Your compliance requirements should drive encryption decisions, not platform convenience.
- Identify data classification requirements
- Understand residency and sovereignty requirements
- Determine key management and rotation requirements
- Plan for audit and reporting needs
Match Encryption Choices to Operational Capabilities: More control over encryption requires more operational capability.
- Provider-managed keys: Good for most use cases, minimal operational overhead
- Customer-managed keys: Better control and compliance posture, moderate operational requirements
- Customer-supplied keys: Maximum control, significant operational complexity
Plan for Cross-Platform Data Movement: When data moves between cloud platforms, encryption compatibility becomes crucial:
- Document encryption standards for data in transit between platforms
- Implement consistent encryption for shared storage solutions
- Plan for key escrow or recovery scenarios
- Consider the performance impact of encryption/decryption during data transfers
Implement Consistent Key Management: If you're using customer-managed keys, consistency across platforms reduces complexity:
- Synchronize key rotation schedules where possible
- Implement consistent key naming and tagging standards
- Plan for key backup and recovery across platforms
- Monitor key usage and access patterns
Tools, Frameworks, and Cloud-Native Integrations That Help
Multi-Cloud Security Platforms: Consider third-party tools that provide unified security management across cloud platforms:
- Prisma Cloud (Palo Alto Networks): Comprehensive cloud security platform
- CloudGuard (Check Point): Multi-cloud security with strong policy management
- Lacework: Behavioral monitoring and compliance across multiple clouds
- Wiz: Agentless security scanning and risk prioritization
Infrastructure as Code Tools: Use infrastructure as code tools that support multiple cloud providers:
- Terraform: Platform-agnostic infrastructure management
- Pulumi: Modern infrastructure as code with multiple language support
- AWS CDK, Azure ARM Templates, Google Cloud Deployment Manager: Platform-specific, but can be used together
Policy Management Frameworks: Implement frameworks that help manage policies consistently across platforms.
- Open Policy Agent (OPA): Policy engine that works across multiple platforms
- Cloud Custodian: Policy management specifically designed for cloud environments
- Config-as-Code: Treat security configurations as code with proper version control
Monitoring and Observability Tools: Implement comprehensive monitoring that spans all cloud platforms:
- Splunk Cloud: Centralized logging and security monitoring
- Datadog: Application and infrastructure monitoring across multiple clouds
- New Relic: Application performance monitoring with security insights
- Native cloud monitoring: Combine AWS CloudTrail, Azure Monitor, and GCP Cloud Logging with central analysis
Identity and Access Management Tools: Choose identity solutions that work well across multiple cloud platforms.
- Okta: Cloud-native identity provider with extensive cloud integrations
- Ping Identity: Enterprise identity management with strong federation capabilities
- Azure AD (Microsoft Entra ID): Strong integration with Microsoft ecosystems and good multi-cloud support
- AWS IAM Identity Center: Primarily AWS-focused, but supports external identity providers
Compliance and Governance Tools: Implement tools that help maintain compliance across multiple cloud environments.
- AWS Config, Azure Policy, GCP Security Command Center: Platform-native compliance monitoring
- CloudCheckr: Multi-cloud cost optimization and compliance
- Evident.io (now part of ESP): Security and compliance monitoring
- Custom solutions: Many organizations build custom compliance dashboards that aggregate data from multiple platforms
Best Practices for Tool Selection:
- Avoid vendor lock-in: Choose tools that support multiple cloud platforms
- Consider integration complexity: More tools mean more integration points and potential failure modes
- Plan for skill requirements: Ensure your team has the skills to operate chosen tools effectively
- Evaluate total cost of ownership: Consider licensing, implementation, and operational costs
- Start simple: Begin with basic multi-cloud capabilities and expand as your maturity increases
Implementation Strategy:
- Assessment Phase: Understand your current state and requirements across all platforms
- Design Phase: Create a target architecture that addresses your specific needs
- Pilot Phase: Implement solutions in a limited scope to validate your approach
- Rollout Phase: Gradually expand implementation across your entire multi-cloud environment
- Optimization Phase: Continuously improve based on operational experience and changing requirements
Remember that the goal isn't to achieve perfect uniformity across all cloud platforms; it's to create a legible, manageable security posture that enables your business while managing risk appropriately. Sometimes platform-specific optimizations make sense, and sometimes consistency is more valuable than optimization. The key is making these decisions consciously and documenting them clearly for future reference.
Conclusion
Navigating cross-cloud security isn't just about understanding individual platforms—it's about creating coherent strategies that work across different providers while meeting your business needs. As we've seen throughout this exploration, AWS, Azure, and Google Cloud Platform each bring unique strengths