By 2025, Zero Trust has transitioned from a conceptual ideal to a practical requirement for organizations prioritizing cloud solutions. As critical workloads span SaaS, IaaS, and hybrid environments, security teams face mounting pressure to implement identity-driven controls that adapt to scale and speed. While Zero Trust is often positioned as the solution, its effectiveness depends entirely on how it is applied; misalignment with the dynamic nature of cloud environments can quickly expose policy gaps, blind spots, and operational friction.
What Is Zero Trust Security in the Cloud?
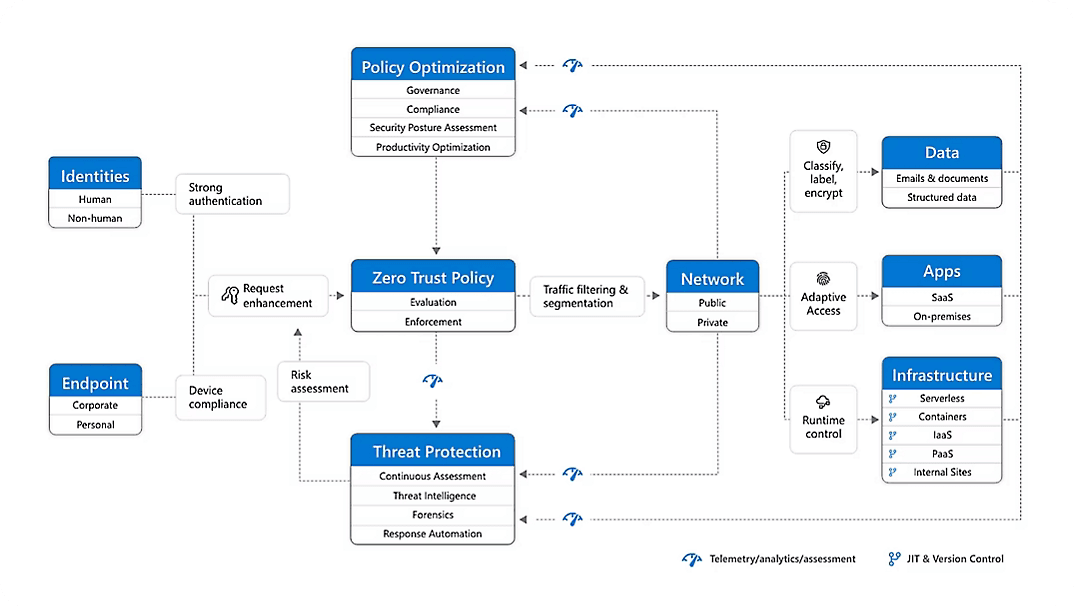
Source - Azure
Zero Trust Security in the cloud is a strategic framework designed to protect cloud environments by enforcing strict identity verification and access controls at every level. Unlike traditional perimeter defenses, Zero Trust assumes that no user, device, or workload—whether inside or outside the cloud network- should be trusted without continuous verification.
Key principles of Zero Trust in cloud environments include:
- Continuous Authentication and Authorization: Every access request, whether from a user or service, is verified in real-time before granting permissions.
- Least Privilege Access: Users and applications receive only the minimal access necessary to perform their tasks, reducing exposure from compromised accounts.
- Micro-Segmentation: Cloud resources are divided into small, isolated segments so that even if one segment is breached, attackers cannot move laterally.
- Comprehensive Visibility and Analytics: Monitoring cloud activity to detect unusual access patterns or behaviors that indicate potential threats.
Cloud-specific factors such as federated identities across multiple SaaS applications, dynamic resource provisioning via APIs, and multi-cloud complexity make Zero Trust both critical and challenging to implement effectively.
The most common errors arise from treating Zero Trust as a checklist implementation rather than an evolving operational strategy.
Let’s explore six specific mistakes organizations are making in 2025, and how to avoid them.
Mistake #1: Treating Zero Trust in the Cloud as a One-Time Project
A common mistake in implementing Zero Trust for cloud environments is treating it as a fixed-scope initiative - planned, executed, and considered complete. While project management structures help with initial rollout, they do not consider the dynamic nature of cloud ecosystems.
Cloud Environments Demand Continuous Security
Cloud environments change rapidly:
- New applications and services are deployed frequently
- Teams add integrations or third-party tools without security team's involvement
- Cloud service providers update APIs, identity models, and security capabilities
- Attackers increasingly exploit cloud misconfigurations and unmonitored services
A global enterprise declared its Zero Trust cloud deployment complete in 2024. However, a major breach occurred the following year due to an unmonitored SaaS integration added after the initial implementation. The Zero Trust model had not adapted to new cloud activity.
The Strategic Approach
Zero Trust in the cloud must operate as a continuous program, not a one-time rollout. Key principles include:
- Ongoing governance: Regularly review access policies, trust boundaries, and integration points to reflect changes in cloud usage.
- Cloud-native visibility: Implement tools that monitor authentication patterns, cloud service changes, and user behaviors in real time.
- Built-in adaptability: Embed trust evaluation processes into development pipelines so that new cloud deployments automatically trigger security assessments.
A technology firm with a multi-cloud setup uses monthly security reviews across its cloud infrastructure. New APIs, SaaS platforms, and cloud-native apps undergo Zero Trust validation before integration. This approach has reduced their exposure to misconfigured services and unauthorized access incidents.
Mistake #2: Ignoring the Principle of Least Privilege
While organizations may adopt identity verification under Zero Trust, many overlook least privilege, restricting users to only the access necessary for their role. In cloud environments, where access controls can be complex and dispersed, this becomes a significant risk.
Cloud-Specific Access Challenges
Cloud platforms often make it easier to grant access than to manage or revoke it:
- IAM roles in platforms like AWS or Azure are often over-permissioned
- Service accounts and credentials are not always removed when no longer needed
- Permissions are frequently assigned based on group membership rather than task relevance
For example, a user in a cloud data team received temporary access to a sensitive dataset for a reporting task. That access remained active months later, long after the task was completed. This pattern, access granted but rarely reviewed or revoked, is widespread.
According to security data from early 2025, compromised credentials were responsible for a large portion of cloud breaches. The severity of those breaches was often due to excessive privileges attached to those credentials.
The Strategic Solution
Applying least privilege in the cloud requires structured, automated access control:
- Role-specific permissions: Define access based on function-specific roles, not broad job titles or department affiliations.
- Temporary access: Use just-in-time models where permissions expire automatically after the task is completed.
- Access reviews: Conduct regular audits of cloud permissions to remove unused or redundant access rights.
- Automatic deprovisioning: Immediately revoke access when users change roles, complete projects, or leave the organization.
A global financial institution implemented automated permission reviews across its hybrid cloud infrastructure. By analyzing access patterns and enforcing expiration policies, they reduced overprivileged accounts by over 60% within six months.
Mistake #3: Assuming Cloud Identities Are Fully Isolated
A frequent oversight in cloud-focused organizations is the assumption that user identities are confined to the boundaries of individual platforms or services. In practice, modern identity architectures are highly interconnected.
Federation, single sign-on (SSO), and directory synchronization create implicit trust relationships that span across cloud services. If a single identity is compromised, attackers can often leverage these trust paths to move laterally between environments without triggering traditional security controls.
Cloud Identity Risks
Cloud environments rely heavily on identity federation, such as Azure AD, Google Workspace, or Okta, to provide seamless access to SaaS platforms, developer tools, and multi-cloud infrastructure. While this improves productivity, it also introduces complex trust relationships across systems that can be exploited.
Consider these common scenarios:
- A user authenticated via SSO to Microsoft 365 can also access multiple Azure services without additional checks.
- A federated identity in AWS is assumed trustworthy across accounts or workloads.
- A compromised identity in Google Workspace is granted OAuth access to third-party apps with overly broad permissions.
Attackers can exploit these connections to:
- Move between services without triggering traditional network-based alerts
- Access cloud-native resources (e.g., storage buckets, CI/CD pipelines) from compromised SaaS platforms
- Escalate privileges using loosely defined trust boundaries across integrated services
What the Data Shows?
Recent incident reports show that 68% of cloud-related breaches involved misuse of federated credentials or service-to-service trust paths. In one case, an attacker compromised a user account with SSO access to both Salesforce and AWS. They exfiltrated customer data by pivoting through an automation tool connected to both platforms, without touching the corporate network at all.
A Modern Defense Strategy
Preventing lateral movement in the cloud means rethinking trust across identities and services:
- Enforce identity context checks: Don’t rely solely on SSO. Use conditional access policies that evaluate risk signals like device health, location, and behavioral anomalies for every access attempt.
- Scope federated access: Ensure federated identities have the minimum permissions necessary within each connected service or cloud account. Avoid assuming trust beyond the initial platform.
- Isolate sensitive services: Use workload identity segmentation to separate production, test, and third-party integrations, so one compromised token doesn’t provide blanket access.
- Monitor cross-service activity: Implement cloud-native threat detection (e.g., AWS GuardDuty, Google Chronicle) that tracks identity behavior across services, not just within individual platforms.
A global software company mitigated a major breach attempt by disabling default trust relationships between Azure AD and third-party apps. They implemented scoped OAuth access and conditional re-authentication for high-risk actions, preventing token reuse that would have enabled lateral movement.
Mistake #4: Ignoring Behavioral Signals in Cloud Access Patterns
Many organizations deploy extensive logging and monitoring in their Zero Trust programs but fail to incorporate behavioral intelligence into their cloud environments. As a result, they miss subtle but critical indicators of compromise, especially when attackers use valid credentials to operate within normal technical boundaries.
The Complexity of Cloud User Behavior
Cloud environments involve dynamic interactions that traditional monitoring struggles to interpret:
- Authentications appear valid even when credentials are misused
- Access to APIs, storage, or services seems routine without established baselines
- High-volume activities from federated identities can go unnoticed without cross-platform correlation
For example, an attacker used a legitimate federated identity through Okta to download large amounts of data from AWS S3. Since the login was technically authorized and IAM permissions were correct, the activity was not flagged, despite being unusual for that user.
In multi-cloud and SaaS environments, attackers blend in by appearing legitimate but behave differently from normal users. Without behavioral analysis, such threats remain hidden.
Enhancing Security Through Behavioral Context
To effectively implement Zero Trust in the cloud, focus must shift from mere data collection to intelligent analysis:
- Establish behavior baselines: Define normal login times, resource usage, and access patterns for each cloud identity
- Detect anomalies: Spot unusual activities like out-of-hours access, rapid API calls, or logins from unexpected locations
- Correlate across platforms: Connect identity behavior data from AWS, Azure, Google Workspace, and identity providers like Okta
- Enable real-time alerts: Respond immediately when behavioral deviations occur, even if authentication succeeds
A digital services firm improved threat detection by integrating behavioral analytics across Google Cloud and Okta. This approach identified insider threats and account compromises that their legacy monitoring missed, reducing incident response times significantly.
Behavioral intelligence provides the missing context needed to complete Zero Trust visibility in the cloud.
Mistake #5: Failing to Align Cloud Security with Business and Operations Teams
Cloud security and Zero Trust are often viewed solely as IT responsibilities, resulting in security controls that don’t align with actual business processes and operational requirements. This gap becomes more pronounced as cloud adoption accelerates across departments outside traditional IT management.
The Impact of Organizational Misalignment in the Cloud
Cloud environments amplify common alignment issues:
- Shadow IT and SaaS growth: Business units adopt cloud applications without IT oversight, creating unmonitored risks.
- Non-IT-led cloud adoption: Teams like marketing, sales, and product development often drive cloud usage, requiring security policies that reflect their workflows.
- Region-specific compliance challenges: Cloud services span multiple geographies, making regulatory requirements like GDPR or HIPAA complex and variable across teams.
A global retailer faced repeated compliance violations when their security team implemented uniform controls that didn’t account for differing regional privacy laws and local business practices. Meanwhile, departments continued to use unauthorized SaaS tools, bypassing formal security policies entirely.
Building Effective Collaboration Across Teams
Cloud security requires active collaboration between security, business, and operational teams:
- Cross-functional governance: Establish cloud security councils with representatives from IT, compliance, operations, and key business units.
- Inclusive planning: Involve business and operations early to understand cloud usage patterns and workflows, ensuring security supports rather than hinders productivity.
- Clear communication: Frame security goals in business terms to show how cloud controls reduce risks specific to each team.
- Regulatory and regional flexibility: Customize policies to fit local compliance requirements while maintaining overall security standards.
A multinational financial services company formed a Cloud Security Steering Committee, including legal, sales, and regional managers. This group coordinated cloud adoption efforts and tailored security controls to regional regulations and operational realities. As a result, unauthorized SaaS usage dropped by 45%, and compliance incidents decreased substantially.
Mistake #6: Believing Cloud Providers Enforce Zero Trust for You
A critical misconception among organizations operating in the cloud is that Zero Trust is already handled by the cloud provider. While platforms like AWS, Azure, and Google Cloud offer robust security capabilities, they do not enforce Zero Trust by default. The shared responsibility model clearly outlines that configuration, enforcement, and monitoring of these controls fall on the customer.
The Shared Responsibility Gap
Cloud providers secure the infrastructure, but the configuration and enforcement of Zero Trust principles rest with the customer. This distinction is often misunderstood:
- Misconfigured storage buckets: Publicly accessible AWS S3 buckets or Azure Blob containers can expose sensitive data, even when basic security controls exist.
- Overly permissive identity scopes: OAuth tokens in Google Workspace or Microsoft 365 can grant more access than necessary if not carefully restricted.
- Implicit trust between services: By default, many cloud services can interact with each other unless strict identity policies are in place.
A retail logistics provider suffered a major data exposure when internal shipping records were left publicly accessible in a misconfigured AWS S3 bucket. Despite operating in a heavily regulated environment, the assumption that AWS "secured everything by default" led to critical gaps. Security tools were available, but unused, because no formal process existed to apply Zero Trust policies to new cloud assets.
Making Zero Trust Work in the Cloud
To avoid this mistake, organizations must take ownership of security controls and policy enforcement in their cloud environments:
- Policy-driven automation: Use infrastructure-as-code and cloud-native policy engines to automatically enforce Zero Trust principles for new services.
- Identity and context validation: Extend Zero Trust logic to all cloud access points, including serverless functions, APIs, and third-party integrations.
- Posture assessment: Regularly audit configurations across cloud accounts to identify and remediate misalignments with Zero Trust expectations.
- Security baselines: Define and apply minimum access and encryption standards across multi-cloud environments, not just the most visible services.
A healthcare network addressed this challenge after discovering over-permissioned OAuth access between its productivity suite and several third-party SaaS tools. Rather than relying on the platform defaults, the IT and compliance teams collaborated to enforce granular permission scopes, isolate third-party access via brokered identity controls, and integrate automated alerts for scope violations. This remediation effort not only aligned with HIPAA requirements but also prevented similar misconfigurations across the organization’s other cloud-connected services.
Building a Sustainable Zero Trust Strategy
Avoiding the six critical mistakes outlined above requires more than technology, it demands a long-term strategy that embeds Zero Trust into your organization’s security culture, business priorities, and operational model. A sustainable approach includes three core elements:
Executive Alignment and Governance
Zero Trust initiatives cannot succeed without support from business leadership. Security leaders must:
- Position Zero Trust as a business resilience program, not just a technical upgrade
- Secure dedicated investment for continuous improvement
- Establish clear governance models and cross-functional accountability
Phased, Business-Aware Implementation
A Zero Trust rollout should be gradual and guided by real business context. Begin with:
- Mapping critical assets, user roles, and data flows across your cloud environments
- Prioritizing high-risk areas such as unmanaged SaaS usage or over-permissioned identities
- Launching pilot projects in departments open to security collaboration, then scaling proven strategies.
This step-by-step method reduces disruption and ensures practical outcomes at each stage.
Metrics That Matter
Zero Trust progress must be measurable to stay effective and improve over time. Core metrics include:
- Reduction in unnecessary or excessive permissions
- Time to detect and respond to anomalous behavior
- Coverage of identity-based access controls across cloud and hybrid systems
- User adoption rates and satisfaction with access experiences
By aligning Zero Trust with operational needs, phasing implementation carefully, and tracking meaningful outcomes, organizations can build a security posture that adapts to change without falling into the common traps.
Building Resilience Through Continuous Alignment
Sustainable Zero Trust in the cloud requires ongoing collaboration between security teams, business operations, and tech teams. When these groups are fully aligned, security measures evolve in step with organizational growth and shifting threat environments, transforming Zero Trust from a one-time project into a dynamic, ongoing practice that adapts proactively to new challenges.